In today’s digital age, businesses are increasingly turning to remote door access solutions to enhance security and streamline entry management. A modern door access control system allows organizations to manage entry permissions from anywhere, providing convenience while ensuring only authorized individuals gain access.
Access control has existed in some form for centuries. In ancient times, city gates were protected by guards who determined who could enter and who could not. Secret knocks, passcodes, and even wax seals were used as early methods of verifying identity and controlling access. As societies advanced, metal keys and locks became the standard for securing doors, but these physical solutions came with limitations, such as the risk of lost keys or unauthorized duplication. Today, access control has evolved into sophisticated electronic systems that offer enhanced security and convenience, leveraging biometrics, mobile authentication, and cloud technology.

What is a Door Access Control System?
A door access control system is a security solution designed to regulate and monitor entry to a building or specific areas within a facility. Unlike traditional lock-and-key mechanisms, modern door control systems utilize digital authentication methods such as keycards, biometrics, PIN codes, and mobile credentials to grant or restrict access. These systems provide businesses with greater security, flexibility, and efficiency by eliminating the risks associated with lost keys and unauthorized duplication.
The best door access control systems leverage advanced technologies like cloud-based management, remote door access capabilities, and integration with surveillance and alarm systems. This allows businesses to monitor and manage entry points from anywhere, ensuring that only authorized individuals can access secured areas. By using a centralized dashboard, security teams can track access logs, set user permissions, and receive real-time alerts in case of unauthorized attempts.
A well-implemented door control system not only enhances security but also improves operational efficiency. Employees can use mobile apps or access cards to enter designated areas without the need for physical keys, while administrators can easily modify access permissions as needed. Whether for small businesses, corporate offices, or high-security facilities, a modern door access control system is an essential component of a comprehensive security strategy.

Everyday Scenarios Where Access Control is Used
Access control is everywhere, often operating behind the scenes in ways we don’t even realize. Here are some common scenarios where door control systems and remote door access technology play a crucial role:
- Residential Complexes & Parking Lots: If you live in a multi-complex residential building with a parking area, access control is in place. License Plate Recognition (LPR) technology scans your vehicle’s plate and grants automatic entry.
- Office Buildings & Workplaces: Employees use keycards, PIN codes, or mobile credentials to enter offices, ensuring only authorized personnel have access.
- Hotels & Hospitality: Many hotels use keycard or mobile access systems for guest rooms, restricting access once a guest’s stay ends.
- Hospitals & Healthcare Facilities: Sensitive areas such as pharmacies, operating rooms, and patient records storage are secured using biometric authentication or card access.
- Airports & Public Transportation: Airports rely on sophisticated access control systems for secure employee-only zones, baggage handling areas, and boarding gates.
- Retail & Warehouses: Employees require authentication to access stockrooms or high-value merchandise areas, reducing theft risks.
- Educational Institutions: Universities and schools use access control to restrict entry to dormitories, laboratories, and administrative offices.
Access control systems are deeply integrated into modern life, ensuring security, convenience, and efficiency across industries. Whether you’re scanning a badge, entering a PIN, or using facial recognition, these systems help manage and monitor access with ease.

How Does a Door Access Control System Work?
A door access control system functions through a coordinated process of authentication, authorization, monitoring, and enforcement. Below is a breakdown of how these systems work:
1. Authentication & Credential Verification
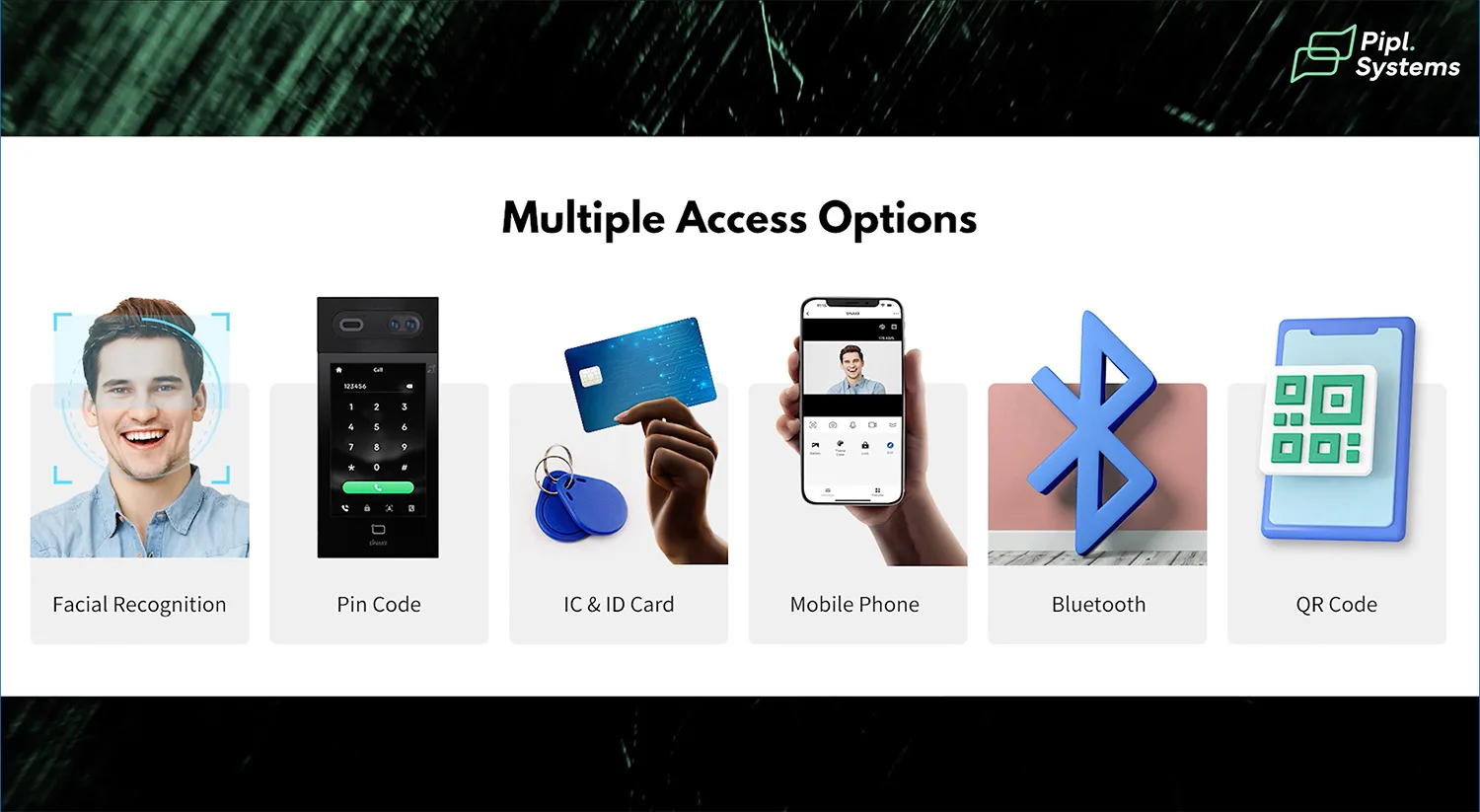
When an individual attempts to gain entry, the door control system first verifies their identity. This can be done through:
- Keycards or Fobs: Scanned on a reader, checking against the database.
- Biometric Authentication: Fingerprint or facial recognition for unique identification.
- Mobile Credentials: NFC or Bluetooth-enabled smartphones acting as digital keys.
- PIN Codes: Numeric access codes entered on a keypad.
2. Authorization & Access Decision
Once authentication is verified, the system determines whether the individual has permission to enter. Advanced access control systems enforce:
- Role-Based Access Control (RBAC): Users are assigned access based on their job role.
- Time-Based Restrictions: Access may only be granted during specific hours.
- Antipassback Protection: Prevents credential reuse by restricting re-entry until exit is logged.

Enhanced RBAC Features
Some of the best door access control systems take RBAC a step further by introducing conditional presence-based access. This means:
- Certain users cannot enter an area unless another designated role is present. For example, a junior employee may not be able to enter a restricted lab unless a senior technician is also inside.
- This feature ensures critical security measures, compliance with regulations, and prevents unauthorized access to sensitive areas without supervision.
- RBAC can also be linked to dynamic access rules, adjusting permissions based on shifts, roles, and real-time personnel tracking.
3. Door Unlocking & Entry Control
If authorization is successful, the system sends a signal to unlock the door. If access is denied, an alert may be triggered, notifying security teams.
4. Real-Time Monitoring & Event Logging
Modern access control solutions track every entry and exit, logging:
- Timestamps of Access Events for security audits.
- Unauthorized Attempts & Lockout Alerts for security personnel.
- Remote Door Access Updates, allowing administrators to control access in real-time.

5. Advanced Security Features & Integrations
- Remote Lock & Unlock Capabilities: Admins can override access remotely via cloud management.
- Integration with Surveillance Systems: Video logs are linked to access events for verification.
- Two-Factor Authentication (2FA): Users may need to present a secondary credential for enhanced security.
6. Emergency Override & Lockdown Procedures
Many access control systems offer emergency protocols, such as:
- Panic Mode: Locks down all doors in case of security threats.
- Fire Alarm Integration: Automatically unlocks exits during emergencies.
A modern door access control system is far more than a digital lock—it is an intelligent security framework designed to protect people and assets while maintaining seamless operations.

Cloud vs. On-Premise Access Control
When selecting the best door access control system, businesses must decide between cloud-based and on-premise solutions. Each option has its own advantages and challenges, depending on the organization’s security needs, budget, and IT infrastructure.
Cloud-Based Access Control
Cloud-based access control systems store access data on remote servers and can be managed via an online dashboard or mobile app. These systems offer:
- Remote Management: Administrators can update access permissions, monitor entry logs, and lock/unlock doors from anywhere.
- Scalability: Cloud systems allow easy expansion across multiple locations without requiring extensive hardware investments.
- Automatic Software Updates: Security patches and new features are rolled out seamlessly without requiring IT intervention.
- Lower Upfront Costs: Most cloud solutions operate on a subscription-based model, reducing initial investment costs.
However, cloud-based access control may be dependent on internet connectivity, and organizations handling sensitive data may have concerns about third-party data storage.

On-Premise Access Control
On-premise access control systems store all data locally, with servers hosted within the organization’s infrastructure. Benefits include:
- Greater Data Control: All access logs and permissions remain within the company’s network, reducing third-party risks.
- No Internet Dependency: Since data is stored locally, system functionality remains intact even if the internet connection is down.
- Highly Customizable: Businesses with complex security needs can configure their system to meet industry-specific compliance requirements.
However, on-premise solutions typically require higher upfront costs, dedicated IT management, and regular maintenance to ensure security updates and system functionality.
Which One is Right for You?
Hybrid Solutions combine both approaches, using cloud-based control with local failover systems for added redundancy.
Small to mid-sized businesses with multiple locations may benefit from cloud-based access control for easy scalability and remote management.
Enterprises handling sensitive data (such as healthcare, finance, or government institutions) may prefer on-premise solutions for greater data security.

The Future of Door Access Control Technology
Following the advancements in cloud-based and on-premise access control solutions, the future of access control technology is shifting towards smarter, more automated, and highly integrated systems. Emerging innovations are shaping how businesses and individuals manage security, emphasizing efficiency, convenience, and data-driven decision-making. Here are some emerging trends shaping the future of door access control systems:
1. AI-Powered Access Control
Artificial Intelligence (AI) is transforming security by analyzing access patterns, detecting anomalies, and predicting security threats before they happen. AI-driven facial recognition and behavioral biometrics are making access control smarter and more adaptive.
2. Blockchain for Access Management
Blockchain technology is being explored as a means to enhance security and decentralize credential management. By leveraging blockchain, access logs can be tamper-proof, ensuring greater transparency and security.

3. IoT-Integrated Access Control
The Internet of Things (IoT) is enabling seamless integration of access control systems with other smart devices. For instance, IoT-enabled locks can communicate with security cameras, alarms, and even HVAC systems to optimize security and energy efficiency.
4. Mobile & Wearable Access
Smartphones, smartwatches, and wearable devices are becoming key tools for access control. Mobile credentials using NFC or Bluetooth allow users to unlock doors without physical keys or access cards.
5. Cloud & Edge Computing for Access Management
Cloud-based access control continues to grow, but edge computing is emerging as a solution to enhance processing speeds and reduce reliance on central cloud servers. By processing access requests locally, edge computing minimizes latency and enhances security.

6. Biometric Advancements & Privacy Considerations
Advanced biometric solutions, such as palm vein recognition and gait analysis, are making access control more secure. However, privacy regulations like GDPR and CCPA require careful handling of biometric data to ensure compliance.
7. Hybrid Access Control Models
Hybrid systems combine cloud-based convenience with the security of on-premise control, giving businesses more flexibility in managing access.
These trends indicate that access control technology is becoming more intelligent, integrated, and secure, paving the way for a more automated and data-driven security landscape.

Common Challenges & How to Overcome Them
While door access control systems offer significant security benefits, they also come with challenges. Here are some common issues and solutions:
1. Integration with Existing Systems
- Challenge: Many businesses struggle with integrating new access control systems with existing security infrastructure, such as CCTV, alarms, and employee databases.
- Solution: Choose an access control system with open API capabilities, allowing seamless integration with third-party software and hardware.
2. User Resistance & Training
- Challenge: Employees and residents may resist changes, especially when switching from traditional key-based systems to digital solutions.
- Solution: Provide clear training and communication on the benefits of the new system, ensuring ease of use and addressing concerns proactively.

3. Lost or Stolen Credentials
- Challenge: Keycards, PIN codes, and even mobile credentials can be lost, stolen, or shared improperly.
- Solution: Implement multi-factor authentication (MFA) and biometric security to reduce reliance on physical credentials.
4. Cybersecurity Threats
- Challenge: Cloud-based access control systems are vulnerable to cyberattacks, such as hacking and data breaches.
- Solution: Use end-to-end encryption, two-factor authentication, and regular software updates to protect against cyber threats.

5. High Upfront Costs
- Challenge: Installing an advanced access control system can be expensive, especially for small businesses.
- Solution: Consider cloud-based solutions with subscription-based pricing to reduce upfront costs while benefiting from scalable security.
6. System Downtime & Reliability
- Challenge: If an access control system goes down due to server issues or power failures, it can create security risks.
- Solution: Invest in systems with built-in redundancy, backup power supplies, and local failover capabilities.
By addressing these challenges proactively, businesses can ensure their door access control system is both secure and efficient, minimizing risks while optimizing access management.

Leading Access Control System Providers
When choosing an access control solution, selecting the right provider is essential to ensure security, scalability, and seamless integration with your infrastructure. Here are some leading brands offering innovative door access control systems:
1. Aiphone
- Specializes in intercom-based and access control solutions for residential and commercial buildings.
- Offers video door stations, audio intercoms, and standalone or integrated access control solutions.
- Key access control products: AC Series (Aiphone’s door access control system), including AC-10U (standalone keypad access control) and AC-20U (networked access system for multi-door security).
- Compatible with GT Series (multi-tenant video intercom) and IXG Series (IP-based security communication) for complete entry security.
- Offers video door stations, audio intercoms, and integrated access solutions.
- Popular models: GT Series (multi-tenant video intercom), IXG Series (IP-based security communication).
- Offers video door stations, audio intercoms, and integrated access solutions.
2. ProdataKey (PDK)
- Specializes in wireless, cloud-based access control systems with real-time remote management.
- Offers modular and scalable solutions for small to large businesses.
- Key products: Cloud Node (central access control unit), Red Series (wireless door controllers), Touch io (mobile credentialing with Bluetooth proximity detection).
3. Inaxsys (Official ICT Distributor in Canada)
- Provides enterprise-level access control solutions with customized security.
- Specializes in ICT (Integrated Control Technology) products tailored for the Canadian market.
- ICT solutions include Protege GX (enterprise-level access and alarm management) and Protege WX (small to mid-size business access control).
4. HID Global
- The industry leader in secure identity solutions, including RFID-based access control.
- Offers smart card readers, biometric authentication, and mobile access solutions.
- Notable products: HID iCLASS SE Readers, HID Mobile Access for smartphone-based entry, and HID Signo (next-gen smart readers).
5. Brivo
- Pioneers in cloud-based access control, offering seamless remote management.
- Integrates with security cameras, visitor management, and mobile authentication.
- Leading products: Brivo Onair (cloud-based security platform), Brivo ACS100 (smart access control panel).
- Integrates with security cameras, visitor management, and mobile authentication.
6. Lenel S2
- A trusted provider of enterprise-class access control and security management solutions.
- Offers highly scalable and flexible security platforms for large and complex organizations.
- Key products: OnGuard (comprehensive security management platform), NetBox (web-based access control system), BlueDiamond (mobile credentialing solution).
7. Avigilon
- A Motorola Solutions company, providing AI-powered access control and video security solutions.
- Integrates access control with advanced video analytics for a comprehensive security approach.
- Key products: Access Control Manager (ACM) (enterprise-grade access control platform), H4 Video Intercom (secure visitor management with video verification), Avigilon Alta (cloud-native access control system with AI integration).
Comparison Table: Leading Access Control System Providers in North America
| Brand | Core Focus | Notable Products & Technologies | North America Presence | Key Differentiators | Integration & Ecosystem |
|---|---|---|---|---|---|
| Aiphone | Intercom-based access control | – GT Series (multi-tenant intercom) – IXG Series (IP-based video intercom) – AC-20U (networked door controller) |
Strong dealer/distributor network in the U.S. & Canada | Trusted in multi-dwelling units (MDUs), schools, and healthcare; award-winning interface design | Seamless video intercom & access control integration; works with legacy systems |
| ProdataKey (PDK) | Cloud-based, wireless access control | – Cloud Node – Red Series controllers – Touch io (Bluetooth mobile access) |
Fast-growing in the U.S.; headquartered in Utah | 100% cloud-native platform; Mobile-first UX; Highly scalable from SMBs to enterprise | Deep integrations with video systems (e.g., Eagle Eye Networks), mobile credentials, and visitor management |
| Inaxsys / ICT | Integrated enterprise solutions | – Protege GX (enterprise-level) – Protege WX (SMB) – Multi-zone alarm integration |
Exclusive ICT distributor in Canada (Inaxsys) | Customizable logic and automation; High-security commercial, government, and industrial focus | Strong BACnet, Modbus, and elevator integrations; centralized alarm & access control |
| HID Global | Identity-based access control | – HID iCLASS SE & Signo readers – HID Mobile Access – Seos Credential Technology |
Widely adopted in government, banking, education, and enterprise sectors | Global leader in secure ID tech; High compatibility with legacy/proprietary systems | Integrates with mobile, biometric, and RFID solutions; partner ecosystem includes LenelS2, Avigilon, Genetec |
| Brivo | Cloud-based, mobile-first access control | – Brivo Onair platform – Brivo Access Control Panels (ACS300/600/1000) – Smart Apartment Integration |
Available across U.S. and Canada; strong in PropTech and real estate | Pioneered cloud-based access in 2001; Robust APIs for third-party platform integrations | Native cloud-to-cloud integrations with Eagle Eye, Identity providers, and visitor management tools |
| LenelS2 | Enterprise-level security management | – OnGuard platform – NetBox for mid-market – BlueDiamond mobile credentials |
Longstanding presence across Fortune 500, airports, and institutions | Recognized for cybersecurity posture; Approved for many U.S. federal/government installations | Deep integrations with fire, intrusion, video (including OnGuard Video), and mobile access apps |
| Avigilon | AI-enhanced access control + video analytics | – Access Control Manager (ACM) – H4 Video Intercom – Avigilon Alta (formerly Openpath) |
Strong U.S. base, backed by Motorola Solutions’ nationwide reach | Uses edge AI for proactive security; H5A analytics and Alta cloud unify access and video at scale | High compatibility with Avigilon video, Motorola Radios, and AI-based threat detection |
Additional Insights: Innovation, Certifications & Strategic Direction in 2025
As of 2025, access control systems are evolving rapidly, driven by cloud-first infrastructure, AI-powered decision-making, mobile-first user experiences, and increased demand for flexible hybrid security environments. Here’s how each of these industry leaders is innovating and positioning their products in the North American market.
Aiphone
- Latest Innovations:
In 2025, Aiphone expanded its IP-based IXG Series with facial recognition and voice assistant integration, enhancing its usability in smart apartments and healthcare facilities. The new IXG AI Gateway supports remote diagnostics, proactive alerts, and multilingual voice commands. - Security Compliance:
UL 294, FCC, and CE certifications. Integrated easily with emergency lockdown systems and ADA-compliant stations. - Use Case Leadership:
Aiphone is a trusted brand in education, senior living, and multi-tenant housing due to its reputation for product longevity and crystal-clear video communication.
ProdataKey (PDK)
- Latest Innovations:
In 2025, PDK launched Touch io v2, which includes geofencing and context-aware unlocking using smartphones and wearables. Their PDK Elevate analytics platform now provides predictive access trends, usage heatmaps, and system health insights via the cloud. - Open Ecosystem:
100+ verified third-party integrations including video, alarms, smart locks, and emergency mass notification systems. - Market Positioning:
PDK is known for offering the most installer-friendly cloud-native access control system in North America. A top pick for co-working spaces, SMBs, and retail franchises.
Inaxsys / ICT (Canada)
- Latest Innovations:
ICT’s Protege GX 2025 release introduced AI-driven access scheduling, biometric compatibility, and integration with machine-learning fire panels. It now supports offline fallback operation, ideal for remote Canadian sites or unstable networks. - Distribution Strategy:
Through Inaxsys, ICT products are now bundled with native video, alarm, and elevator control systems, making them one of the few true unified platforms in the Canadian market. - Target Sectors:
High-trust sectors including municipal infrastructure, utility companies, data centers, and critical infrastructure projects.
HID Global
- Latest Innovations:
The newly launched HID Aero X Series Controllers allow AI-assisted authentication, continuous behavioral biometrics, and zero-trust architecture enforcement. HID’s Mobile Access SDK 2025 enables integration into custom enterprise apps and wearables. - Global Certifications:
Common Criteria EAL6+, FIPS 201-3, ISO 27001 – approved for use in military, banking, and federal government deployments. - Global Influence, Local Adaptation:
HID now supports dynamic authentication profiles, adapting security levels per user or device in real-time.
Brivo
- Latest Innovations:
In 2025, Brivo introduced Brivo Snapshot AI, which auto-generates user access summaries, guest behavior patterns, and system usage anomalies. Its Unified Tenant Experience (UTE) feature integrates visitor access, elevator dispatching, and smart thermostat control in luxury buildings. - PropTech Integration:
Brivo is the go-to for smart apartments, student housing, and office portfolios, with integrations into Yardi, AppFolio, Entrata, and ButterflyMX. - Cloud Reliability:
99.999% uptime with multi-region cloud failover architecture and zero-downtime software updates.
LenelS2
- Latest Innovations:
OnGuard 8.5 now includes AI threat correlation, multi-modal biometric access, and cybersecurity analytics to detect configuration vulnerabilities in real time. LenelS2’s BlueDiamond AI Edge Reader introduces gesture-based unlocking and contextual lockdown scenarios. - Federal Compliance:
LenelS2 maintains full GSA approval, DoD certifications, and is used widely across U.S. military bases, airports, and critical government infrastructure. - Enterprise Analytics:
Real-time access logs are now paired with AI-driven alerts and anomaly detection, empowering operators to respond faster to insider threats.
Avigilon (Motorola Solutions)
- Latest Innovations:
Avigilon’s Alta Access (formerly Openpath) now includes AI facial verification, touchless QR unlock, and live video verification directly from the cloud dashboard. The Avigilon Unity platform merges ACM with License Plate Recognition, video analytics, and emergency call routing. - AI & Cloud Power:
Avigilon’s Alta suite features AI event prioritization, allowing real-time alerts for tailgating, loitering, or unauthorized access attempts, using cloud-based deep learning models. - Unified Security:
A top choice for hybrid environments, Avigilon solutions unify cloud video, access control, and radio communications in a single command interface, popular among school districts, logistics, and healthcare systems.
In short
Door access control systems have evolved into an essential component of modern security infrastructure, helping businesses and individuals manage entry securely and efficiently. From small offices to large-scale enterprises, these systems provide the flexibility, convenience, and protection needed to safeguard assets and personnel.
As technology continues to advance, the integration of AI, cloud-based management, and biometric security is making access control smarter and more adaptive. Whether you are looking for a remote door access solution, a door control system for your workplace, or the best door access control system for an enterprise, understanding the available options will help you make an informed decision.
By evaluating security needs, compliance requirements, and emerging trends, businesses can implement a door access control system that is not only efficient but also future-proof.

FAQs About Door Access Control Systems
1. What is the difference between standalone and networked access control systems?
Standalone access control systems operate independently at a single entry point and are typically used for small businesses or residential buildings. Networked access control systems connect multiple doors and locations, allowing centralized control, real-time monitoring, and integration with other security systems.
2. Can an access control system be integrated with other security systems?
Yes, most modern access control systems integrate with CCTV cameras, alarm systems, visitor management software, and building automation systems. This enhances overall security by allowing seamless monitoring and event-triggered actions.
3. How secure are mobile access credentials compared to traditional keycards?
Mobile access credentials (via NFC or Bluetooth) are generally more secure than keycards because they are encrypted and stored on a personal device. Unlike keycards, which can be easily lost or cloned, mobile credentials often require biometric or PIN authentication for added security.
4. What happens if an access control system goes offline?
Most advanced access control systems have failover mechanisms. On-premise systems will continue to function locally, while cloud-based solutions often have offline mode features that allow stored credentials to be used even when the internet is down.
5. How can businesses protect access control systems from hacking?
To prevent cyber threats, businesses should implement multi-factor authentication (MFA), encrypted communication protocols, regular software updates, and strict role-based access policies. Using cloud-based solutions with end-to-end encryption further enhances security.
6. Is biometric access control better than keycards or PINs?
Biometric access control (e.g., fingerprint, facial recognition) is more secure because it uses unique biological characteristics. However, it can be expensive and may raise privacy concerns. Keycards and PINs are more common due to their cost-effectiveness and ease of implementation.
-
ICT Access Control Case Study: Enterprise Security Upgrade in a Multi-Level Commercial Facility
I’m Jack Dugas from Roger’s Security Systems, and in this detailed ICT access control case study, I’m walking you through an active, in-progress enterprise security upgrade we’re executing at a large multi-level commercial facility in the Burlington/GTA area of Southern Ontario. This project represents a comprehensive modernization of the client’s aging card access infrastructure, integrating […]
-
UniFi Solution for Warehouse: Advanced AI Surveillance for a 77,000 Sq Ft Facility
Hello, I’m Anton Kuznetsov from YesTechie, and I’m excited to share a deep dive into one of our most dynamic UniFi deployments: a massive 77,000-square-foot facility encompassing both warehouse and office spaces. This project presented unique challenges and specific requirements from our client, which is why we’ve chosen to document our process. Our goal with […]
-
Enterprise UniFi Solution for Aerospace Industry Company
We filmed this project in Pennsylvania during a larger enterprise UniFi rollout, where we had already migrated the client’s network to UniFi earlier in the year. This phase was about expanding from “network foundation” into a full unified stack: video (Protect), door access (Access), and alarm/sensor expansion – all managed in one ecosystem. What we […]
-
Full Guide to the New Ajax TurretCam HL with Hybrid illumination
1. Intro: The Problem with Night Vision in Security Cameras I’m Jack Dugas from Roger’s Security Systems, and we’ve been installing security systems in Southern Ontario for over 32 years. Today, we’re working on a residential project where we’re putting in the new Ajax TurretCam HL — the latest in hybrid illumination technology. For years, […]
-
Ultimate Residential Security Guide: A Real‑World Ajax Case Study by Roger’s Security Systems
I’m Jack from Roger’s Security Systems. Together with the Pipl Systems team, we spent two days on a real residential project or Ajax Systems residential case study in Southern Ontario, Canada, filming and documenting a full Ajax Systems installation. This is not a lab demo or show‑room build: Our goal with this project — and […]
-
How to Choose the Right Smart Lock for Your Business in 2025
In a home, one or two people hold the keys. In a business, dozens do. You have staff, cleaners, vendors, temps — and because of that, a business smart lock may open hundreds of times a day, which raises the stakes for reliability, accountability, and speed of management. So, frame the decision correctly. You are […]