This BodyShop Case Study shows how the UniFi Protect Intercom became the backbone of a seamless gate access solution. The installation feels less like a collection of devices and more like a carefully orchestrated system, designed to handle daily comings and goings without friction.
Helder Luis from AIM Security walked us through the setup, explaining how his team stitched together access, video, and alarms into one environment. Watching him demonstrate each feature, it was clear this was more than a technical showcase – it was a live test of how everyday staff and visitors would actually interact with the system.

Who this deployment serves
• Shop owners who want fast Gate Access Control without constant oversight
• Installers seeking clean wiring, PoE-based reliability, and license-free credentials
• Facilities that juggle staff, contractors, and visitors throughout the day
How we tested and why the results matter
Helder guided us step by step as we simulated real access scenarios. We checked enrollment for different credentials, tried unlocking from mobile devices, and measured how quickly the gate responded. At every point, the intercom doubled as a camera, feeding constant video into Protect for accountability. This gave us confidence that the system wasn’t just working – it was recording context around every access event.

The integrated security system in practice
When you combine access, video, and alarms in one place, things get simpler. Staff can see who’s at the gate, talk to them, and approve entry, all while knowing that any alarm elsewhere in the shop will still reach their phone. This level of integration turns a potential juggling act into a single smooth workflow.
Pick up your UniFi products via our affiliate link:
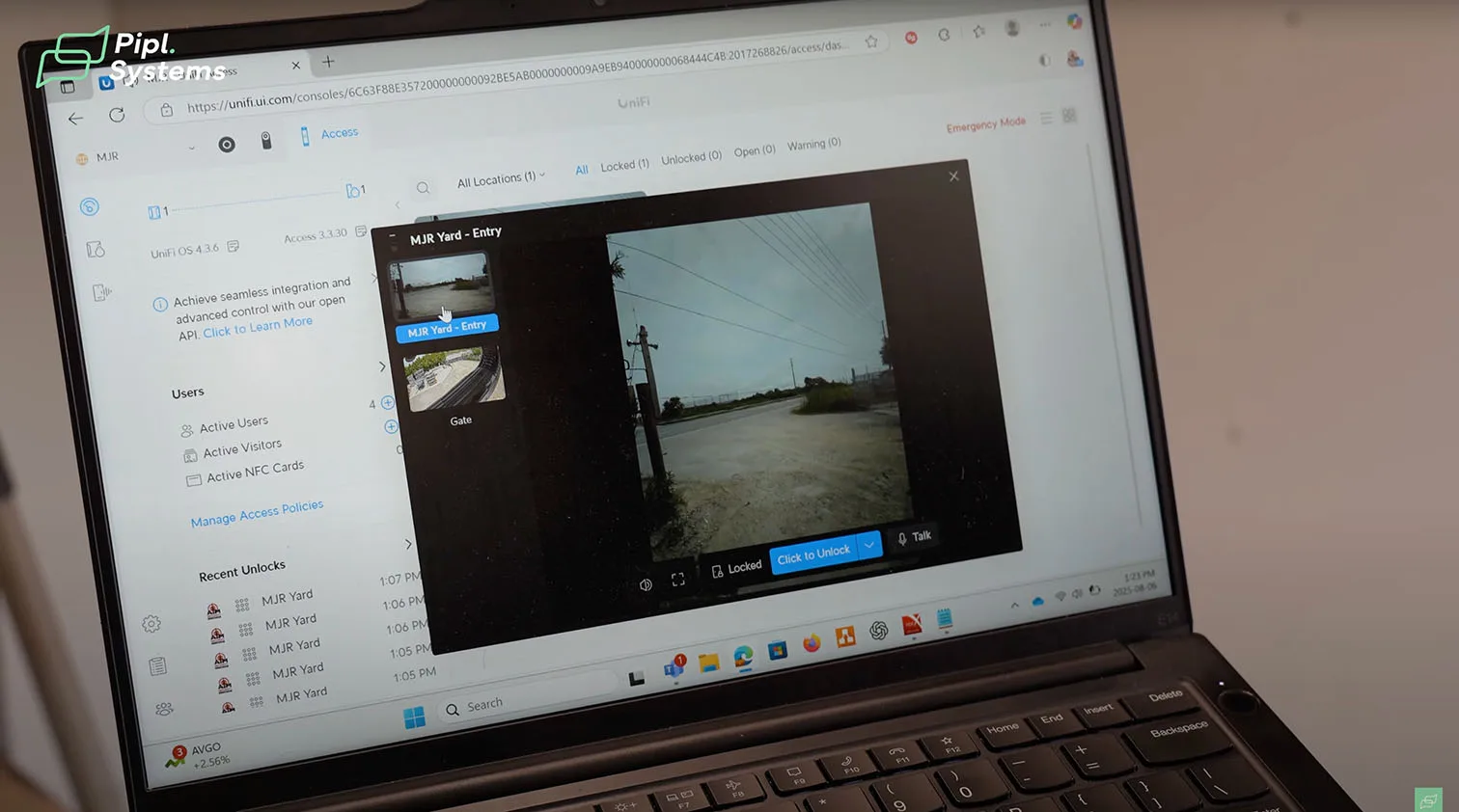
Gate entry via UniFi UA-Intercom: walk-up flow and credentials
Helder showed us what it feels like to approach the intercom at the main gate. The camera was already live, recording in Protect, before he touched anything. Visitors can scroll through a directory, press the call button, or simply start a two-way audio intercom for gates. On the other side, staff answer on their phone, see who’s there, and open the gate with a tap.
Walk-up flow step by step
- Step up to the station and face the camera
- If enrolled, the face recognition intercom system unlocks the gate automatically
- If not, choose a directory contact or press the call button
- The operator answers and verifies the visitor
- Entry is granted, while all events are captured for later review
Available authentication methods
The intercom doesn’t force a single approach. Instead, it lets you pick what fits each user.
• Face recognition for regular staff with predictable routines
• NFC card for contractors or temp workers who need controlled access
• QR code for visitors and deliveries with limited time windows
• PIN keypad as the universal fallback
• Mobile app unlock for managers who often work away from the desk
Why this intercom was chosen
Helder explained that the decision came down to durability and versatility. A metal, weather-resistant design withstands Canadian winters and summer rain. The top light ensures faces are visible at night, which improves both recognition and video clarity. Because it records 24/7 as part of the Protect ecosystem, there’s always context for each unlock. Add to this the license-free credential management, and the choice made itself.
Reliability at night and in daily use
• Always-on recording adds accountability
• Integrated light helps recognition after dark
• Microphone and speaker carry clear audio even with background noise
• Mobile unlock cuts wait times when staff are away from the office
Credential methods at a glance
| Method | Hands free | Offline capable | Best use case | Notes for backup |
|---|---|---|---|---|
| Face recognition | Yes | Yes | Daily staff with regular routines | Always enroll a second method |
| NFC card | No | Yes | Contractors, temporary staff | Collect cards on last day |
| QR code | No | Yes | Visitors, scheduled deliveries | Keep windows short |
| PIN keypad | No | Yes | Universal backup | Change codes after turnover |
| Mobile app unlock | No | Partial | Managers approving remotely | Ensure app login is active |
Practical notes from the field
Helder stressed that default PINs should never be left active, even during testing. Face templates work best when enrolled under steady lighting and then checked again at night with the built-in light. For guests, QR codes and directory calls are the quickest options while still maintaining security.
Deployment of AI Security Cameras: perimeter coverage that earns trust
Helder walked the perimeter first, then the interior lanes where vehicles idle and staff move constantly. The team placed UniFi AI Turret Cameras at choke points and corners so each lens held a clear angle on faces and plates without relying on digital zoom. This created an AI-powered video surveillance layer that feels responsive rather than showy, the kind of coverage that catches real movement and gives operators useful evidence.
What these cameras actually detect in daily use
People detection, face recognition, license plate reading, and sound detection are not bullet points here; they are the workhorses that flag motion that matters. On approach, the camera tags a person, pairs the moment with clear audio, then logs the event in Protect so operators can pull the clip without hunting. In busy yards, this precision cuts review time and reduces false positives that fatigue a team.
Vandal resistance and why it matters outdoors
The vandal-proof housing survives accidental hits and weather that shifts from freeze to rain in a single day. Mounts were tightened with thread compound, conduit paths stayed short and sealed, and the result is a camera that keeps recording when forklifts or box trucks come too close.
Light, identification, and the blue ring
The spotlight triggers on motion, which does two things at once. It improves identification after dark, and it signals to a visitor that recording is active. The blue ring animates on detection, so people know the system saw them. That subtle cue reduces risky behavior at the edge of the property.
Two way audio and situational awareness
Operators can speak through the camera without leaving the desk, confirm who is at the door, or redirect a delivery to the correct bay. Audio becomes the bridge between video and action, useful when hands are full or when a driver cannot find the right contact.
Placement checklist for integrators
• Cover approach vectors, not empty walls
• Angle for faces first, plates second, then wide context
• Keep cable runs protected and short with PoE budgets verified
• Validate night performance with the spotlight enabled, then fine tune shutter and gain
• Set sound detection thresholds during normal shop noise, not silence
Feature to outcome table for AI Turret deployments
| Camera capability | Practical outcome for operators | Where it helps most |
|---|---|---|
| People detection | Fewer false alerts, faster review | Two-way audio |
| Face recognition | Confident identification at the gate | Main approach, check in doors |
| License plate reading | Vehicle traceability during disputes | Drive lanes, loading zones |
| Sound detection | Awareness of atypical noise events | After hours monitoring |
| Spotlight on motion | Better night identification, deterrence | Dim corners, exterior doors |
| Two way audio | Resolve issues without dispatching staff | Bays, side gates, temporary entrances |
Advantages of the UniFi Protect ecosystem: one stack, less friction
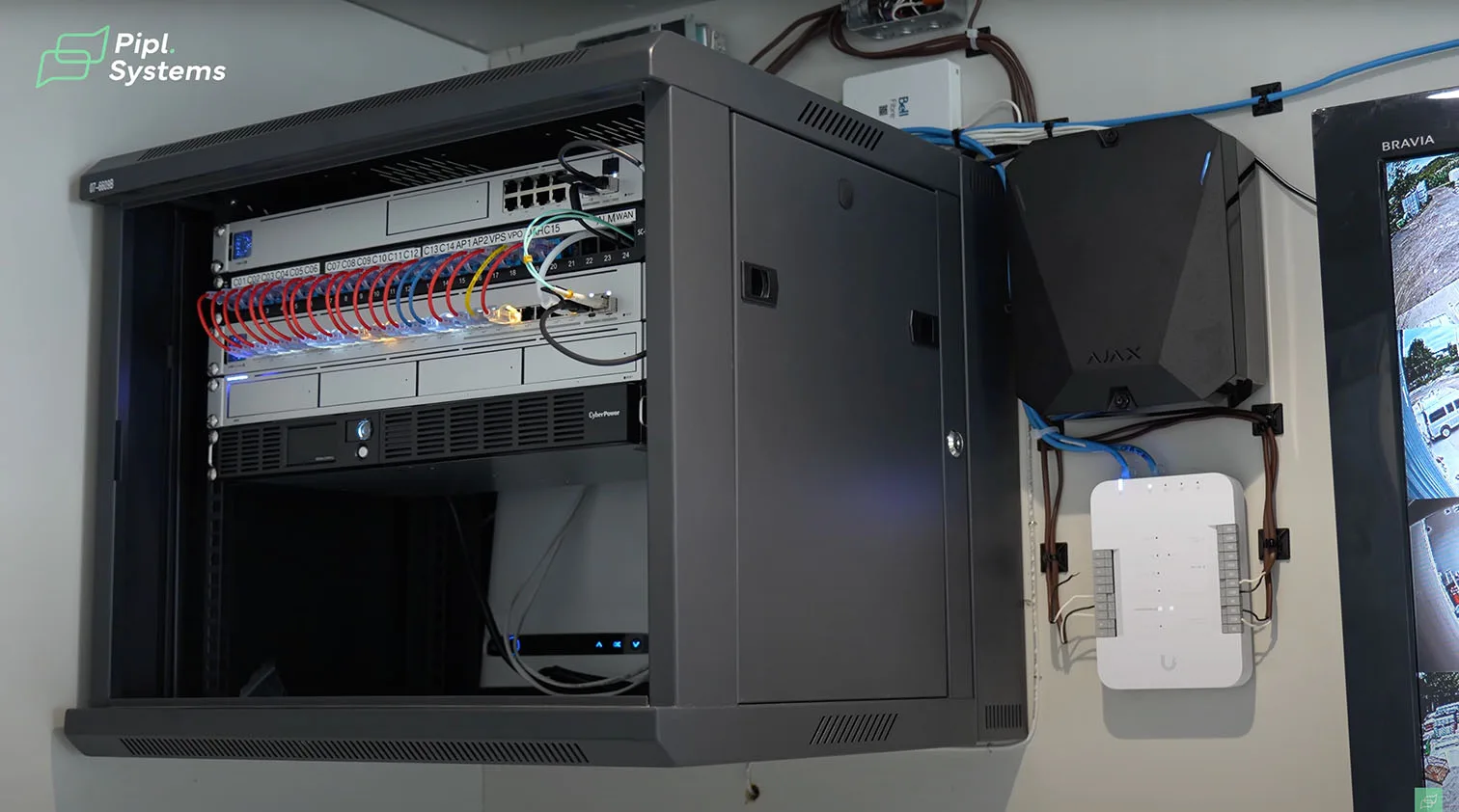
Inside the rack, the design stays simple on purpose. Each device does a job, everything speaks the same language, and the operator experience remains consistent from the gate to the office. That predictability is what makes this Ubiquiti Protect case study useful for shops that need results today, not just features on a spec sheet.
Core components that anchor the system
The control plane lives on a UniFi Dream Machine Pro SE, storage runs on a UniFi UNVR Network Video Recorder, displays use UniFi ViewPort for clean live walls, switching relies on a UniFi 24 Port Pro Max Switch, and access control events route through a Ubiquiti UniFi Access Hub. A dedicated UPS power backup for security systems keeps recording and access functional during brief outages so evidence and entry do not disappear when the lights flicker.
Why operators prefer a unified workflow
A single login, a single place to search, and one event timeline that ties video to access. Staff answer a call, see video, speak to the visitor, and grant entry without switching tools. When incidents occur, the clip, the time, and the unlock action align cleanly for audits and incident reports.
What this looks like during a typical day
Helder demonstrated a delivery arriving while interior work continued. The gate call popped up, the operator checked the video, approved entry, and logged the delivery while cameras inside continued to capture movement around the equipment. No one paused to juggle apps or chase a method that only one person knew how to use.
Rack level roles and practical notes
| Device | Role in the stack | Practical note for deployment |
|---|---|---|
| UniFi Dream Machine Pro SE | Network, security policies, remote access | Create VLANs for cameras and access devices |
| UniFi UNVR Network Video Recorder | Continuous recording and retention | Size storage to match required retention days |
| UniFi 24 Port Pro Max Switch | PoE delivery and aggregation | Verify PoE budgets for turrets and the intercom |
| UniFi ViewPort | Dedicated live monitor output | Place one in the office, one in the shop |
| Ubiquiti UniFi Access Hub | Access control logic and I/O | Tie door position sensors and relays here |
| UPS power backup for security systems | Keeps video and access alive during outages | Budget runtime for at least safe shutdown |
The access layer is inside the same pane of glass
The gate intercom and the access hub live in the same ecosystem, so unlocks, door position changes, and alarms correlate with camera clips automatically. That alignment saves time when reconciling deliveries, investigating damage, or training new staff on opening and closing routines.
Why does a single vendor reduce the total cost?
Licensing remains predictable, credential management does not add recurring per-user fees, and updates land through a known channel. Fewer moving parts means fewer failures and faster support when something needs attention. For AIM Security and teams like it, this translates to quicker handoffs and fewer callbacks after commissioning.
Ecosystem takeaways for North American buyers
• Use one stack when you want video, access, and alarms aligned for audits
• Pick hardware that tolerates cold mornings and wet afternoons without drama
• Treat the UPS as part of the system, not an accessory
• Keep the ViewPort screens where decisions happen, not in a back room
Monitoring And Access Control Hub: Rack Design, VLANs, And Device Onboarding
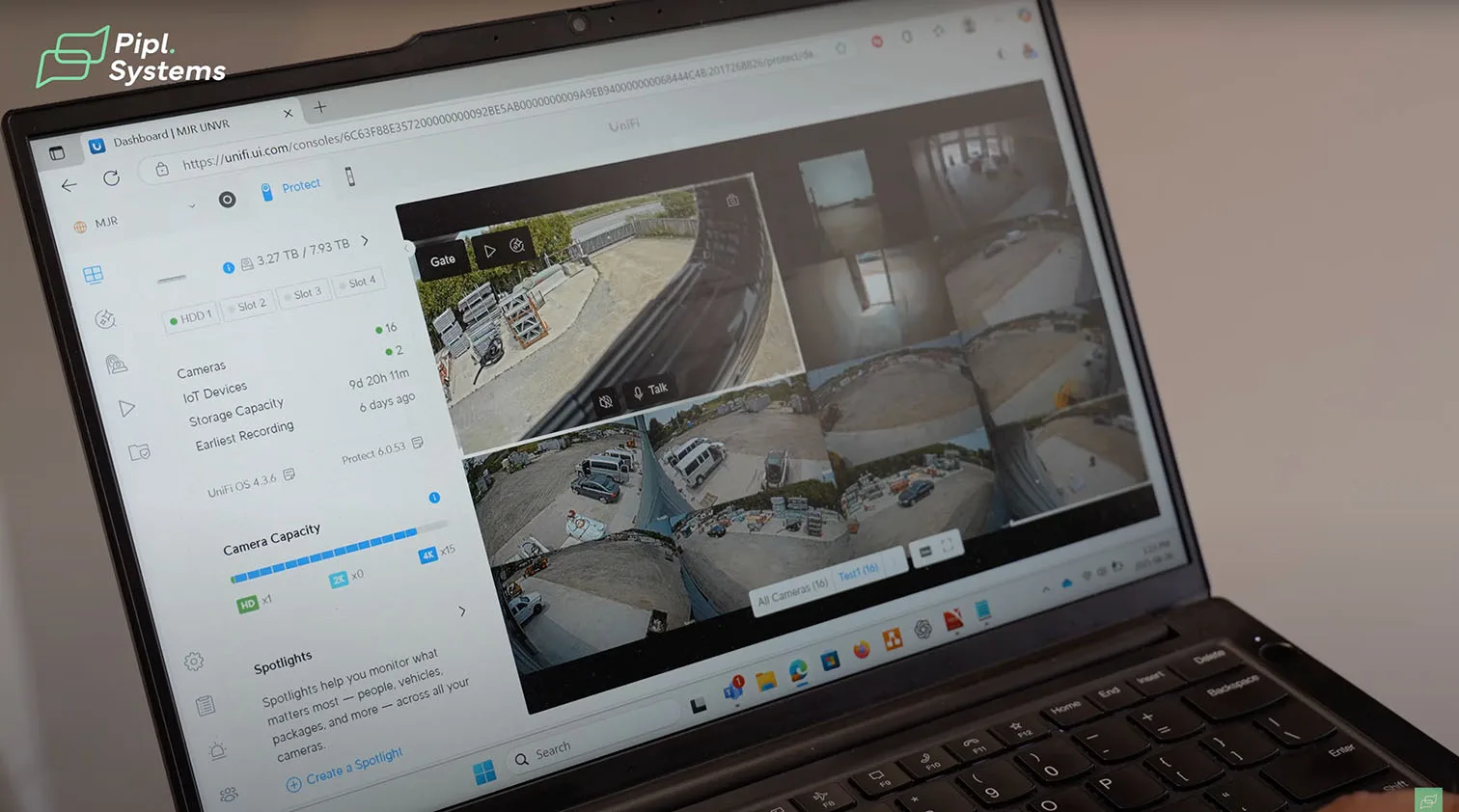
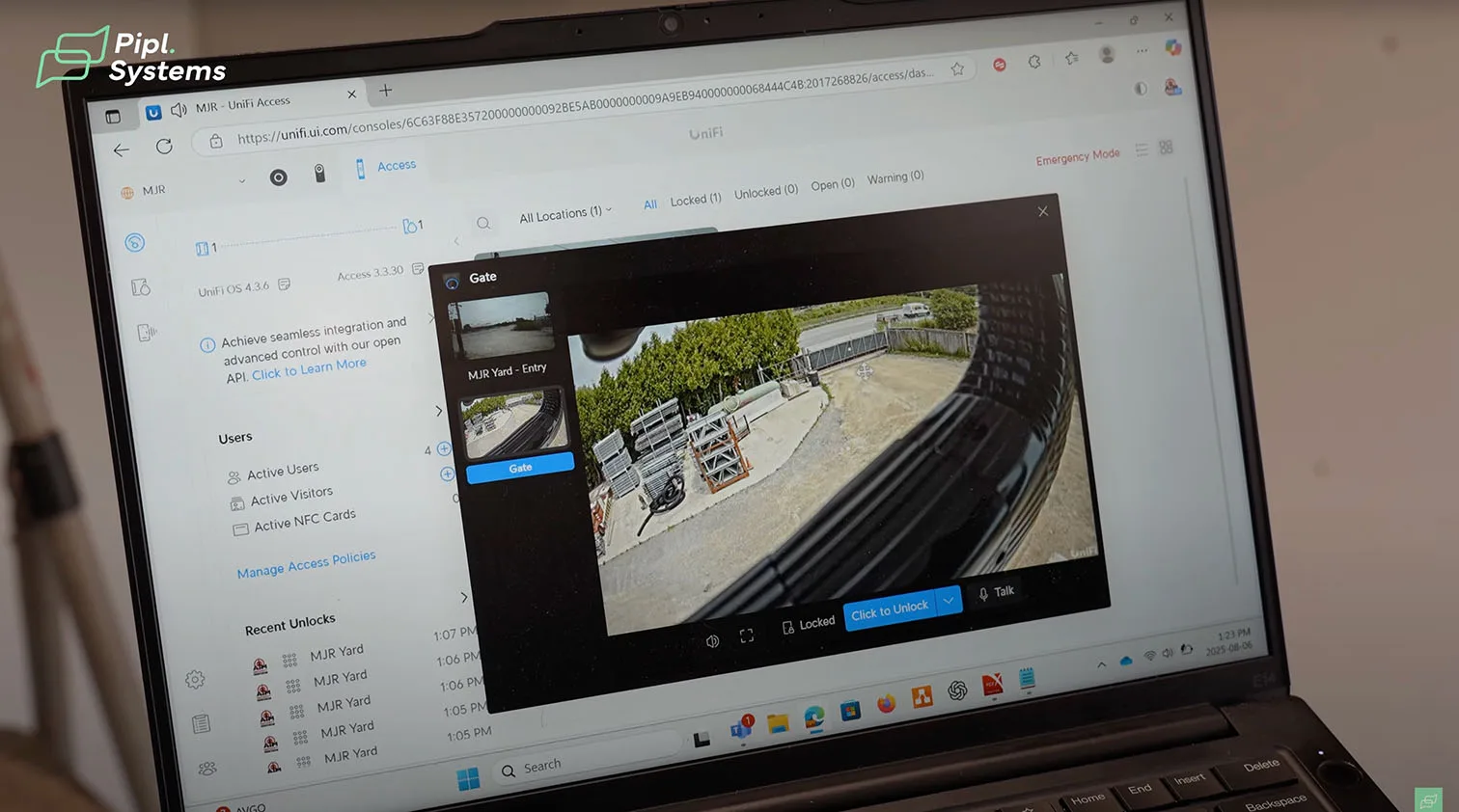
The future office already runs a live monitor wall, one screen in the office and one in the shop, driven by UniFi ViewPort for constant camera awareness. Helder routed the gate station to a Ubiquiti UniFi Access Hub, where relays and inputs handle gate triggers, a third-party doorbell, and a door position sensor that reports open and closed states in real time. This keeps Gate Access Control visible to operators without leaving the camera view.
Operator Screens And Daily Workflow
Operators can watch the yard on the ViewPort, answer a call from the intercom, and confirm the visitor while the archive keeps recording inside Protect. If your team is new to Protect, start with our step-by-step UniFi Protect guide for beginners. It explains consoles, recording, and event review in a way that helps first-time users adopt a professional workflow: UniFi Protect guide for beginners.
Access Hub Wiring And Clean I/O
The access hub sits between the intercom and the gate hardware. Relays control the strike or operator, inputs watch the door position sensor, and a simple buzzer adds audible confirmation in the shop. Because access logic and video live in the same ecosystem, unlocks and door state changes align with recorded clips without juggling apps.
Rack Layout And Power Considerations
The rack houses a UniFi Dream Machine Pro SE for policy and control, a UniFi UNVR for continuous recording, a UniFi 24 Port Pro Max Switch for PoE, and a UPS power backup for security systems to ride through short outages. A labeled patch panel terminates camera home runs, ViewPort feeds, access points, the access hub, and the alarm head end. This is the kind of deliberate build AIM Security is known for, neat cabling and predictable service loops.
VLAN Segmentation And MAC Filtering That Actually Block Misuse
Helder segmented traffic by function. Cameras live on a camera VLAN, office devices on a user VLAN, access devices on their own access VLAN. The outside Ethernet drop that reaches the gate is locked down with MAC filtering so only the intercom and the access hub can authenticate on that port. That simple policy stops someone from plugging a laptop into the exterior jack to ride the network.
Quick Reference Table For The Hub And Rack
| Component | Purpose In The Stack | Deployment Note For Reliability |
|---|---|---|
| Ubiquiti UniFi Access Hub | Relays, inputs, and credential events | Land door position sensor on supervised input |
| UniFi ViewPort | Live camera output to TV displays | Create a camera and access VLANs with ACLs |
| UniFi Dream Machine Pro SE | Network control, policies, remote management | Create camera and access VLANs with ACLs |
| UniFi UNVR | Continuous recording and retention | Size storage to incident review requirements |
| UniFi 24 Port Pro Max Switch | PoE and aggregation for all edge devices | Verify PoE budgets for intercom and turrets |
| UPS Power Backup For Security Systems | Keeps access and video running during brownouts | Budget runtime for clean shutdown if needed |
Where The Deeper Access Guide Fits
If you plan to expand door readers, intercoms, or add new unlock methods, review our complete UniFi Access 3.0 walkthrough. It covers reader setup, credential types, and the nuances of event auditing in the UniFi Access interface: UniFi Access 3.0 walkthrough.
Centralized Management Via UniFi Site Manager: One Console For Network, Protect, And Access
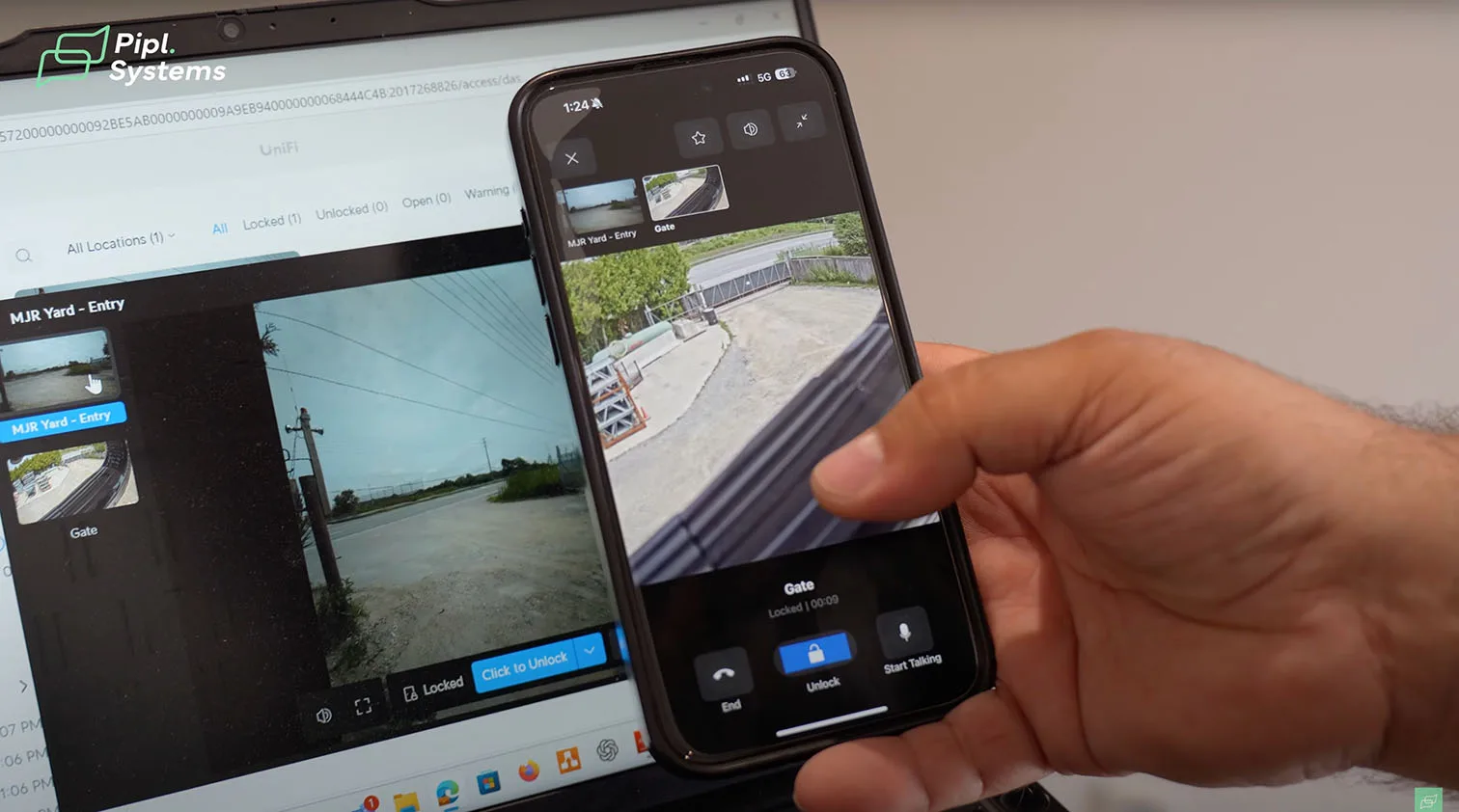
The site runs with UniFi Site Manager, so network, Protect, door access, and the control plane sit under a single login. In practice, this means an operator can click into cameras, then into access events, then into network health without leaving the dashboard. Helder paired the gate camera and the intercom so staff can check gate status on mobile and unlock from the same screen.
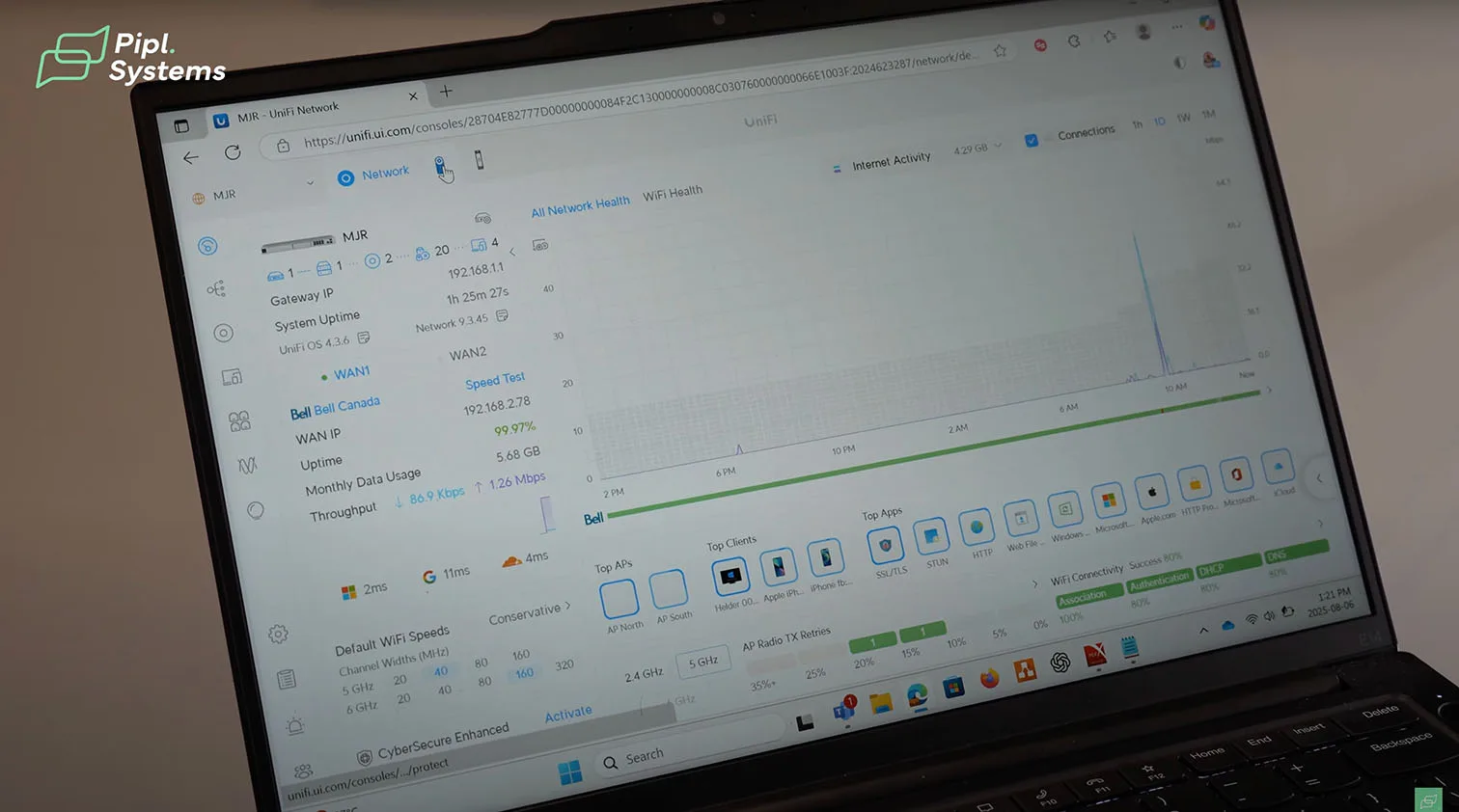
What Operators See In A Normal Shift
From the dashboard, the camera at the gate shows who is waiting. A single tap moves to the intercom view, audio opens, and the unlock appears when the operator is satisfied with the verification. If the door position sensor reports an unexpected open state after hours, the event timeline already has the matching video clip ready to review. This is a true integrated security system where video, access, and alarm data converge.
How Pairing Improves Gate Status Checks
Pairing the gate camera with the intercom view reduces guesswork. You can confirm the approach, confirm the identity, and confirm the mechanical state of the gate before and after the unlock. The same pairing helps during training because new operators learn the visual flow in minutes.
Admin Tips That Keep Multi-Role Teams Sane
Use role-based access so managers can approve unlocks from mobile while technicians only see video feeds. Keep a short list of saved views for shift leads, for example, a two by two mosaic of entry points that covers the main gate, the yard, the shop door, and reception.
Control Surfaces At A Glance
| UniFi Surface | Primary Job For The Operator | Why It Matters Day To Day |
|---|---|---|
| Protect Cameras View | Live and recorded video | Evidence without exporting between tools |
| Access Events Timeline | Unlocks, credentials, door state | Instant audit trail for deliveries and visits |
| Network Health | Device uptime, PoE budgets, adoption status | Faster troubleshooting when something drops |
| Mobile App Quick Actions | Answer intercom, remote unlock, acknowledge | Gate decisions happen from the yard |
Where are Alarm Monitoring Layers In
If you plan to escalate events to a monitoring workflow, see our field guide on AI video alarm monitoring with UniFi Protect and Chekt. It shows how to route verified alarms to operators so they see the right clip at the right time, not a wall of noise: AI video alarm monitoring with UniFi Protect and Chekt.
Closing Notes For Managers And Integrators
The value of UniFi Site Manager is not only visibility, but it is the rhythm it gives a team. Cameras, access, and network share a common language, so training runs faster and handoffs are cleaner. When you add a device, it adapts into the same structure. When you troubleshoot, logs tell a single story. That is why this Ubiquiti Protect case study resonates with busy shops; it replaces tool switching with decisions.
Pick up your UniFi products via our affiliate link:
Ajax Alarm System Integration With MultiTransmitter
What The Panel Adds To The Stack
The alarm layer complements access and video, not competes with them. Ajax Alarm System brings supervised intrusion protection that speaks the same operational language as your gate workflow. The board on site supports eighteen zones with clean wire management and power options in two locations, which keeps retrofit paths open for doors, motions, and perimeter contacts without clutter in the rack.
MultiTransmitter Use Cases And Sensor Mix
MultiTransmitter lets you blend legacy wired loops with new wireless devices. You can migrate door contacts and motion zones by zone while adding modern detectors, where pulling cable is impractical. The result is a flexible intrusion map that grows with the facility without forcing a cutover day.
Enrollment, Scenarios, And Operator Clarity
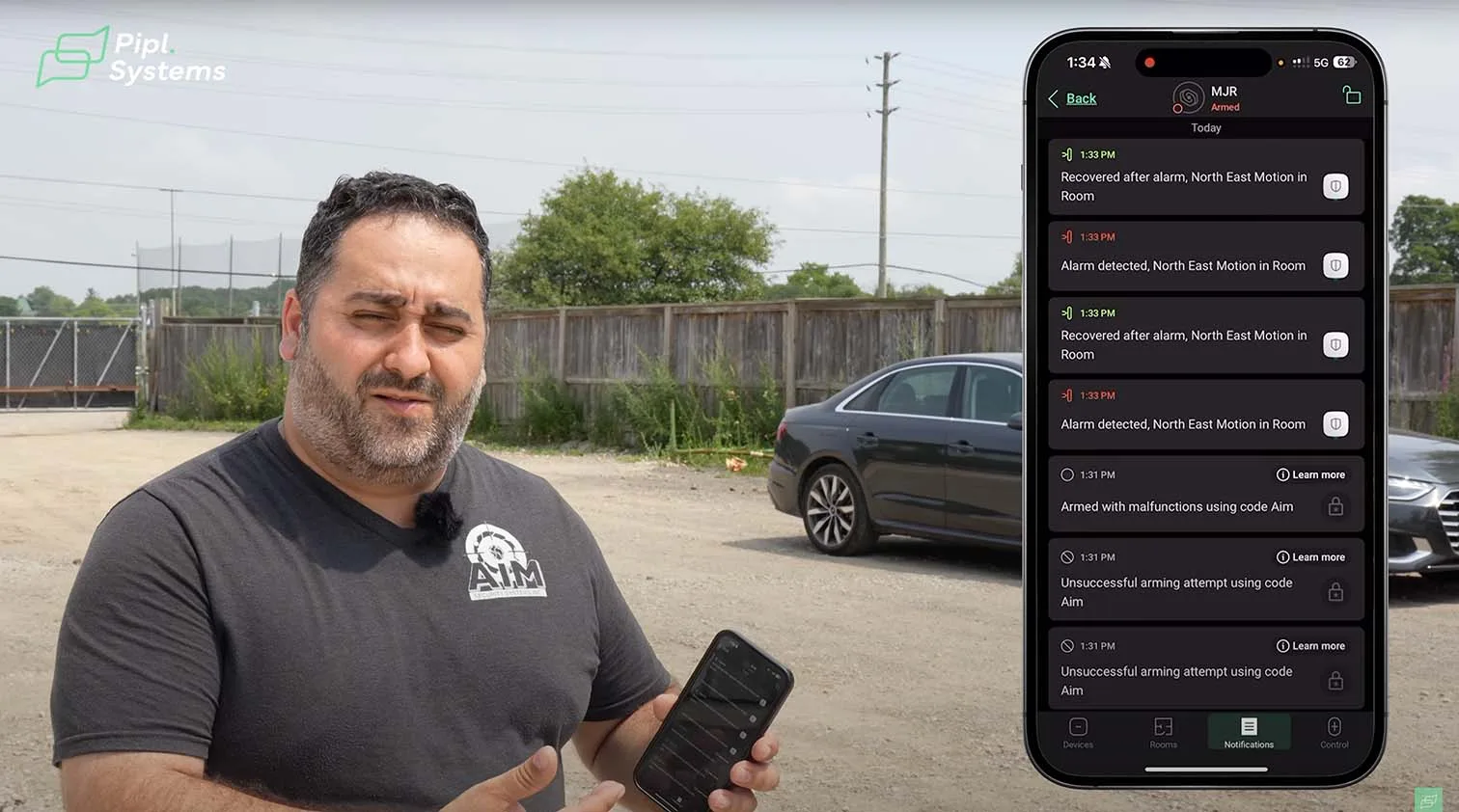
Helder handled enrollment in a predictable order, then attached simple scenarios to common events. Arm the shop, confirm door states, notify the team if a bay stays open, and route a siren event to the mobile app for immediate acknowledgement. Scenarios reduce the number of taps an operator makes during opening and closing, which is where mistakes often creep in.
Power, Supervision, And Test Cadence
Two power injection points simplify distribution to remote zones. Supervision intervals remain short enough to catch failures without spamming operators. A monthly walk test verifies siren output, strobe visibility, and event paths to the monitoring station. AIM Security documents the results in a simple checklist that lives near the rack.
Quick Configuration Table For MultiTransmitter
| Task | What To Verify | Field Note For Reliability |
|---|---|---|
| Zone mapping | Loop type, resistor values | Label at the can and at the rack |
| Power budgeting | Standby and alarm current | Leave headroom for cold starts |
| Supervision timing | Tamper, loss of signal, low battery | Align with nightly arm schedule |
| Scenario logic | Arm, disarm, auto bypass rules | Keep exception paths short and clear |
| App notifications | Severity and recipients | Train on acknowledge and escalate |
For readers building a gate first system, this entry pairs well with our UA-Intercom Gate Access Starter Kit guide, which explains device roles and unlock paths from the approach to the relay: UA-Intercom Gate Access Starter Kit guide.
Ajax KeyPad TouchScreen And StreetSiren In Action
Arming Flow And What Operators See
The KeyPad TouchScreen presents a clean interface. Disarmed shows as an open circle, arm and night modes sit one tap away, panic options for fire and medical stay visible but out of the way. Helder armed the system with the main door intentionally open to show how the panel flags an issue before the countdown begins, which is the kind of feedback that prevents false trips.
NFC Convenience And Panic Behavior
NFC cards offer quick arm and disarm for trusted staff, which keeps codes private and reduces credential sharing. Panic actions create immediate, unmistakable events, useful during after hours when voice calls waste time. The screen responds quickly and resists fingerprints, which matters on a shop floor where hands are never perfectly clean.
StreetSiren Output And Visibility
The StreetSiren combines sound with a strong strobe, so people nearby understand that an alarm occurred even if machinery drowns out the tone. Helder triggered motion to demonstrate the full cycle. The app received the alert, the monitoring station saw the same event, and the team confirmed test mode before proceeding. That closed loop is what turns sensors into action.
Mode Overview At A Glance
| Mode Or Action | Typical Use | What The Team Should Confirm |
|---|---|---|
| Arm | End of day, full perimeter | All doors closed, no active bypass |
| Night | Staff inside, perimeter only | Interior motions bypassed by policy |
| Disarm | Start of shift, deliveries | First person in verifies alarm memory |
| Panic Fire | Visible smoke, heat event | Evacuate first, then acknowledge |
| Panic Medical | Injury or health incident | Send location with the notification |
Unified Security For Real World Needs
What This BodyShop Case Study Proves
A single pane of glass changes the rhythm of a workday. Operators answer the call at the gate, view the video, talk through the speaker, and approve entry, while the alarm layer stands ready to escalate true intrusion. This is an integrated security system that joins video, access, and alarm into one workflow that people actually use.

Buyer Takeaways For North American Shops
Start with the approach, keep Gate Access Control fast, then layer the Ajax Alarm System for credible alerts that arrive with context. Treat cameras as evidence engines, not decorations. Size storage for retention that matches how long disputes take to surface, then train the team to pull clips without hesitation.
Final Notes On Reliability And Handover
Helder Luis from AIM Security showed how careful commissioning prevents headaches later. Helder’s path from device wiring to enrollment to scenario testing is the template we recommend. Mention AIM Security once more as a reminder of the professional standard behind this build, then keep the playbook simple. Consistent labels, short SOPs, and a rack that tells a clear story. This Ubiquiti Protect case study demonstrates that when UniFi Protect Intercom handles the front door and Ajax handles intrusion, the result is a system that protects people and time, not just property.
Expert Insights on Integrated Security
Why Unified Systems Win In Real Operations
North American businesses want fewer moving parts and faster answers when something happens. A unified stack turns video, access, and alarms into one story. Operators see the visitor at the gate, confirm identity, check the door position sensor, and log the event in a single flow. This is where an integrated security system delivers value that pieced together tools rarely match.

Outcomes That Matter To Owners And Integrators
• Lower total cost of ownership through license-free credentials and predictable storage planning
• Faster training because UniFi Site Manager, Protect, and Access share one design language
• Cleaner audits thanks to time-aligned clips, unlock events, and alarm records
• Better uptime when PoE design, VLAN segmentation, and UPS power backup for security systems are planned together
Capability To Outcome Map
| Capability | Business Outcome | Implementation Note |
|---|---|---|
| Gate access tied to UniFi Protect Intercom | Fewer handoffs and quicker decisions | Train staff to use mobile remote unlock |
| AI-powered video surveillance | Faster incident search and fewer false alerts | Tune analytics after a normal week of traffic |
| Centralized role based permissions | Clear separation of duties | Create operator and manager roles up front |
| Unified event timelines | Stronger compliance and easier reporting | Standardize retention targets by site profile |
| VLAN and MAC filtering | Reduced lateral risk on exterior drops | Lock outside ports to intercom and hub only |
Comparison With Traditional Systems
Where The Old Approach Falls Short
Siloed systems look fine on paper until a delivery arrives while an alarm trips inside. Staff jump between apps, video timestamps do not line up, and no one is sure who opened the gate. A combined UniFi Protect case study shows the opposite. One pane of glass. One narrative. Fewer mistakes.
Head To Head Summary
| Dimension | Unified UniFi Protect + Ajax Alarm System | Separate Video And Access Vendors |
|---|---|---|
| Deployment time | Faster, single adoption and policy set | Longer, multiple consoles and playbooks |
| Licensing and credentials | Predictable, license free for access | Often per user fees and renewals |
| Operator training | One workflow for calls, clips, and unlocks | Multiple UIs and retraining after updates |
| Remote operations | Mobile app covers talk, view, and approve | Remote paths differ by vendor and app |
| Incident correlation | Clip, unlock, and alarm aligned by time | Manual export and spreadsheet notes |
| Failure domains | PoE and UPS can be sized as one plan | Mixed power paths and unknown runtimes |
| Scalability | Add readers, cameras, or views with one policy | New gear requires new rules and exceptions |
| Total cost of ownership | Lower, fewer contracts and simpler support | Higher, overlapping maintenance and licenses |
FAQ Section
What Is The Main Advantage Of UniFi Protect Intercom
It anchors Gate Access Control and video in one place. Staff can see the visitor, talk through the station, and approve entry without switching tools. Every decision lands next to a recording that is easy to review later.
Can Ajax Alarm System Work With Wired Sensors
Yes. MultiTransmitter bridges legacy wired zones with new wireless devices. You can migrate in phases and keep doors, motions, and contacts that already work.
How Reliable Is UPS Power Backup For Security Systems
When sized correctly, a UPS keeps recording and access online through short outages and brownouts. Plan runtime for a clean shutdown of the UNVR and intercom, and verify PoE budgets so key devices stay powered.
What Cameras Are Best For AI-Powered Video Surveillance
Perimeter deployments benefit from UniFi AI Turret Cameras. They combine people detection, face recognition, license plate reading, a motion spotlight, and two-way audio. Place them at approach angles where faces and plates are clear.
Does UniFi Site Manager Support Remote Access
Yes. Administrators and operators can manage network health, Protect, and Access remotely. Use role based permissions so managers can approve unlocks while technicians focus on cameras.
How Secure Is NFC And QR Code Access Control
NFC offers strong, convenient credentials for staff. QR codes work well for time bound visitor access. Pair both with PIN fallbacks and log every event in Protect for a complete audit trail.