Active construction sites pose unique security challenges, especially in high-risk zones where heavy machinery like cranes is involved. After working hours, these areas become both a safety hazard and a liability concern. Unauthorized access can lead to accidents, theft, or property damage, and in cases involving large cranes, the consequences can be severe. The priority for site managers is to ensure that no unauthorized person enters these restricted areas during off-hours.
In this particular case, the DSV building group faced a pressing need: to secure a crane zone that required absolute exclusion after hours. The goal was to establish a system capable of instantly detecting intrusions, sending real-time alerts, and enabling a rapid police response.
Key Technologies in Play
The implemented solution integrated three main technologies:
- Alarm monitoring for immediate off-hours breach detection
- UniFi Protect for high-resolution, network-based video surveillance
- CHeKT for video verification, ensuring alerts are tied directly to visual confirmation before escalation
This combination created a layered, video-centric security system that reduced false alarms and enhanced response accuracy.

Why AIM Security Was Selected
Helder Luis, representing AIM Security, led the design and deployment of the solution. His team’s expertise in blending AI-driven video systems with real-time alarm monitoring made AIM Security the ideal partner for this challenge. With a proven track record in high-risk site protection, AIM Security was able to assess the site, identify vulnerable points, and design a system that would provide full coverage without interfering with daily operations.
Their approach emphasized:
- Minimal downtime for installation
- Seamless integration with existing site infrastructure
- Scalable design for future expansion if the site layout changes
On-Site Context and Implementation
As explained by Helder Luis on site, the crane area posed significant safety risks if accessed after hours. His team was tasked with ensuring that any presence in this zone would trigger an immediate, verified alert. In the event of an intrusion, the system would send real-time notifications to the monitoring center, supported by live video feeds, enabling security personnel or law enforcement to act instantly.
This approach not only enhanced safety but also protected the construction company from potential legal and financial liabilities arising from unauthorized site access. It demonstrated how modern AI-powered security solutions can transform risk-heavy environments into controlled, monitored zones — even in complex and evolving construction settings.
Main Controller and System Flow
Site Constraints and Network Design
The construction site’s layout changes daily, with cranes, heavy vehicles, and shifting equipment making long cable runs unsafe and impractical. To overcome these constraints, a hybrid network design was implemented: short PoE runs near fixed power points combined with a secure wireless backbone spanning the active site. This ensured continuous monitoring of the high-risk crane zone during off-hours without interfering with construction activity.
Core Console: Ubiquiti Dream Machine SE
At the heart of the deployment is the Ubiquiti Dream Machine Special Edition, providing routing, PoE switching, and local UniFi Protect recording. Its built-in hard drive bay simplifies storage planning for 4K video, while onboard PoE ports directly power critical devices, including the AI Horn Speaker and UBB wireless bridge.
WAN and Uptime Strategy
Because no wired internet service is available, a cellular WAN connection was chosen as the primary link. A line-interactive UPS ensures the controller, wireless links, and cameras remain powered during short outages, keeping the alarm and monitoring systems online after hours.
Video-to-Alarm Bridge: CHeKT + UniFi Protect
The CHeKT Bridge converts camera views into active alarm zones. Each UniFi camera sends RTSP streams from UniFi Protect to the bridge, allowing the monitoring center to receive real-time video verification when the system is armed. Operators can see live feeds, review event clips, and confirm activity before dispatching police, reducing false alarms and increasing response accuracy.
Webhooks and I/O: Arduino Opta Relay Controller
To connect UniFi’s AI analytics with alarm triggers, an Arduino Opta I/O module was programmed to receive custom webhooks from UniFi Protect Alarm Manager and convert them into relay closures for the CHeKT Bridge. This ensures a fast, direct link between detection events and alarm processing.
Wireless Span: UBB Building-to-Building Bridge
For areas where trenching or running conduit is impossible, a pair of Ubiquiti UBB wireless bridges carries encrypted data from the crane zone to the site control hub. A compact PoE switch at the far end powers the AI PTZ Industrial camera, a fixed 4K AI turret, and the horn speaker.
End-to-End Signal Path
- AI camera detects a person or vehicle in the crane zone
- UniFi Protect Alarm Manager sends a webhook to the Arduino Opta
- Opta closes a relay, feeding an input to the CHeKT Bridge
- CHeKT raises an alarm and sends video with zone metadata to the monitoring center
- AI Horn Speaker and camera spotlights activate for immediate deterrence
- Monitoring operator verifies and dispatches police if required
Why This Architecture Fits Active Construction Sites
This approach clearly divides responsibilities: UniFi Protect for device management and storage, CHeKT for alarm verification, and UBB for flexible, non-intrusive wireless connectivity. It allows high-reliability monitoring even over cellular WAN and in constantly changing job site conditions.
Key Components and Roles (Quick Reference)
| Device | Role in the Flow | Why It Matters |
|---|---|---|
| Ubiquiti Dream Machine SE | Routing, PoE switching, local NVR | Central control for both networking and recording |
| Cellular modem + UPS | WAN + power stability | Maintains monitoring capability during outages |
| CHeKT Bridge | Video verification | Converts camera feeds into alarm events |
| Arduino Opta (I/O) | Webhook-to-relay interface | Links UniFi AI analytics to alarm triggers |
| UBB wireless bridges | Long-distance site link | Maintains high-speed encrypted connections without cabling |
| AI PTZ Industrial + 4K AI turret | Detection coverage | Tracks movement and captures clear evidence |
| AI Horn Speaker | Deterrence + audio talk | Immediate on-site response capability |
This solution, designed and implemented by AIM Security under the direction of Helder Luis, established a fully verifiable off-hours exclusion zone around the crane, protecting both site safety and liability without slowing construction progress.
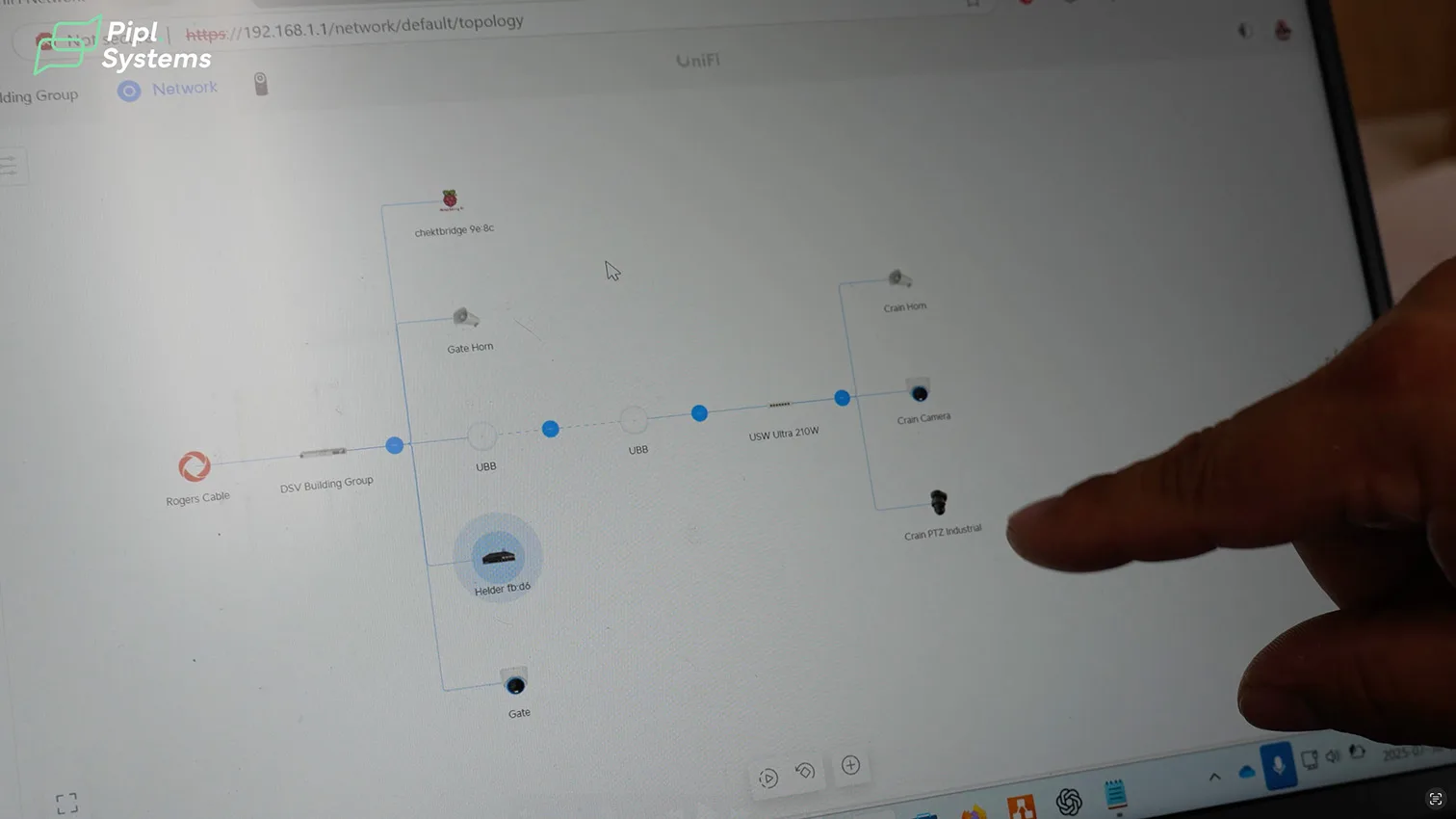
Topology and Interface Overview
What the UniFi Topology Shows
The UniFi Controller Topology view lays out the entire video-centric security system on one line: cellular ISP uplink → Ubiquiti Dream Machine Special Edition (UDM-SE) → USW Ultra PoE switch → UBB wireless bridges → field devices (AI PTZ Industrial, AI Turret 4K cameras, and AI Horn Speakers). The CHeKT bridge sits on the LAN next to the controller, receiving RTSP video from UniFi Protect and alarm inputs from a relay. This visual map makes it easy to verify link health, PoE loads, and which node each device is homed to in real time.
Hybrid Transport: Wired Core, Wireless Edge
AIM Security designed a hybrid network because trenching new cable across an active jobsite was unsafe. Short runs inside the site trailer remain wired for stability; long runs jump by UBB wireless bridges to poles near the crane and gate. PoE from the UDM-SE and the Ultra 210W switch powers horns and cameras, so only one cable reaches each device. This keeps critical links up during daily site changes and heavy-equipment traffic.
Device Inventory and Roles
• AI PTZ Industrial: long-range coverage of the crane zone, patrol presets, and zoomed inspections.
• Fixed AI camera (AI Turret): static view on the gate for person/vehicle detection with 4K clarity.
• AI Horn Speaker: deterrence and live talk-down; plays a custom message when alarms fire.
• CHeKT bridge: the visual security bridge that turns each camera view into a supervised alarm zone for video verification.
• Arduino Opta + PoE splitter: hosts a small webhook service; when UniFi Protect fires a rule, the Opta toggles a relay into the CHeKT bridge.
• UPS and LTE/cellular modem: keep cameras and the controller up during outages so recording and local automations continue.
Protect Interface Walkthrough
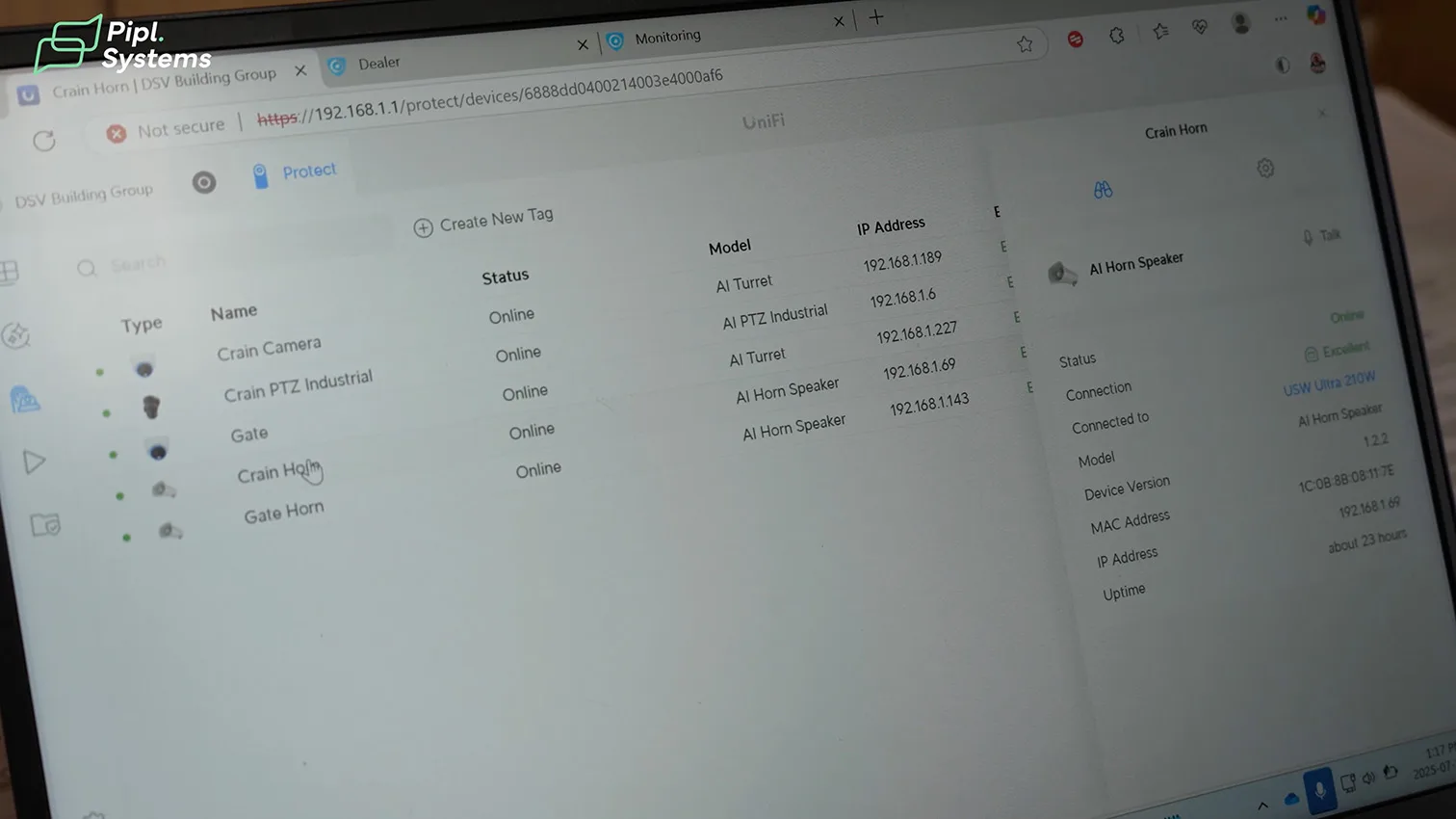
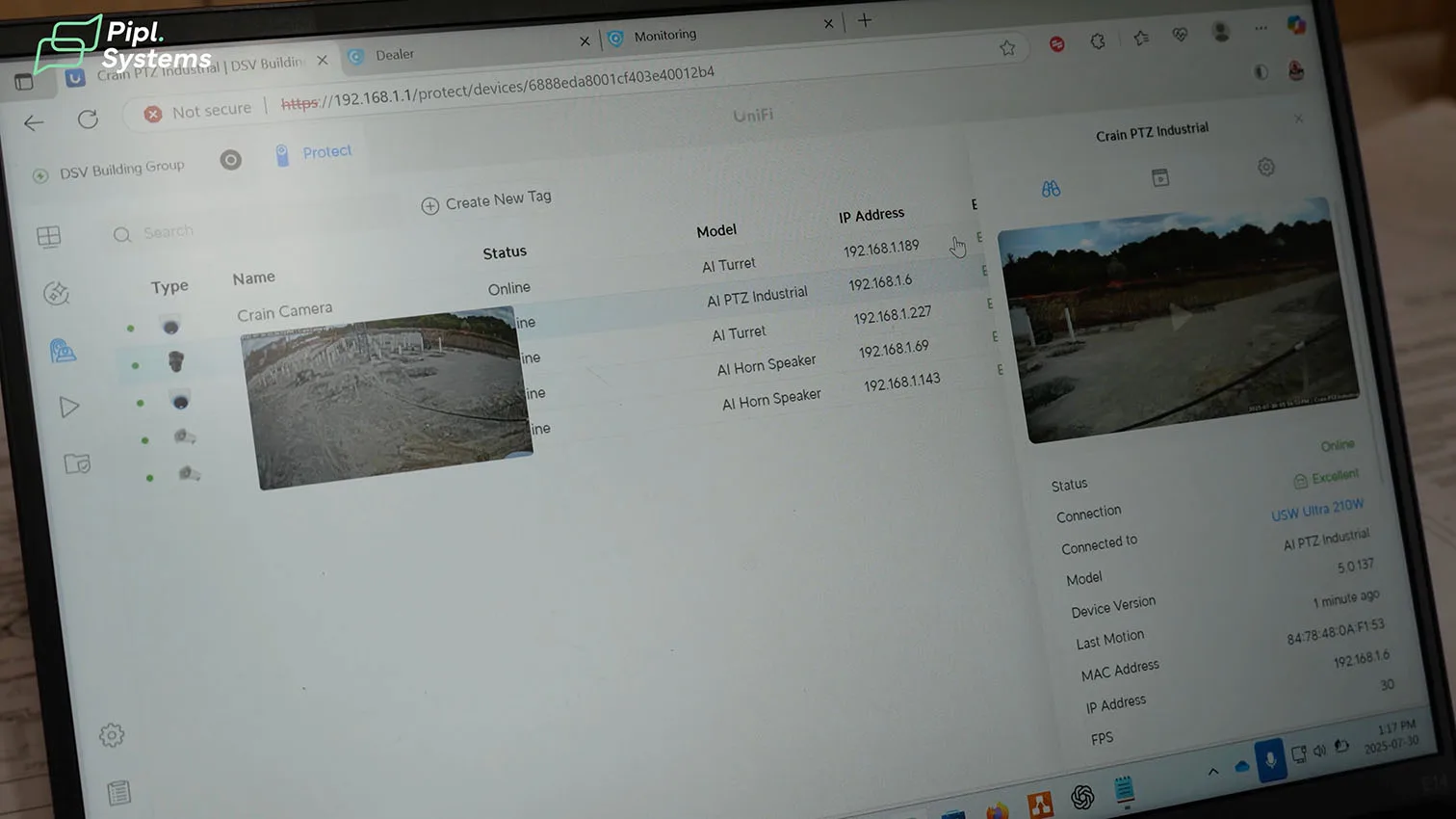
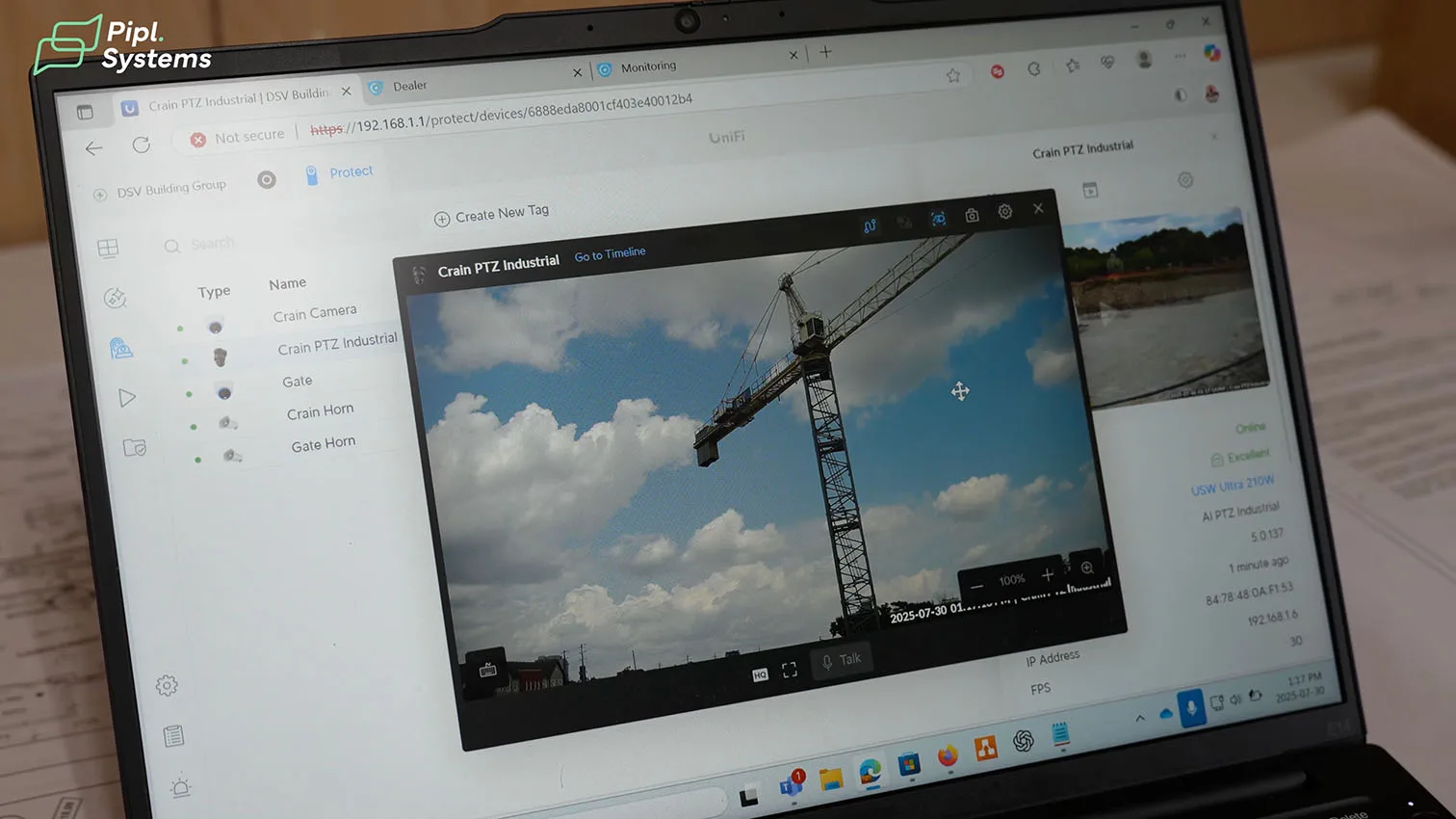
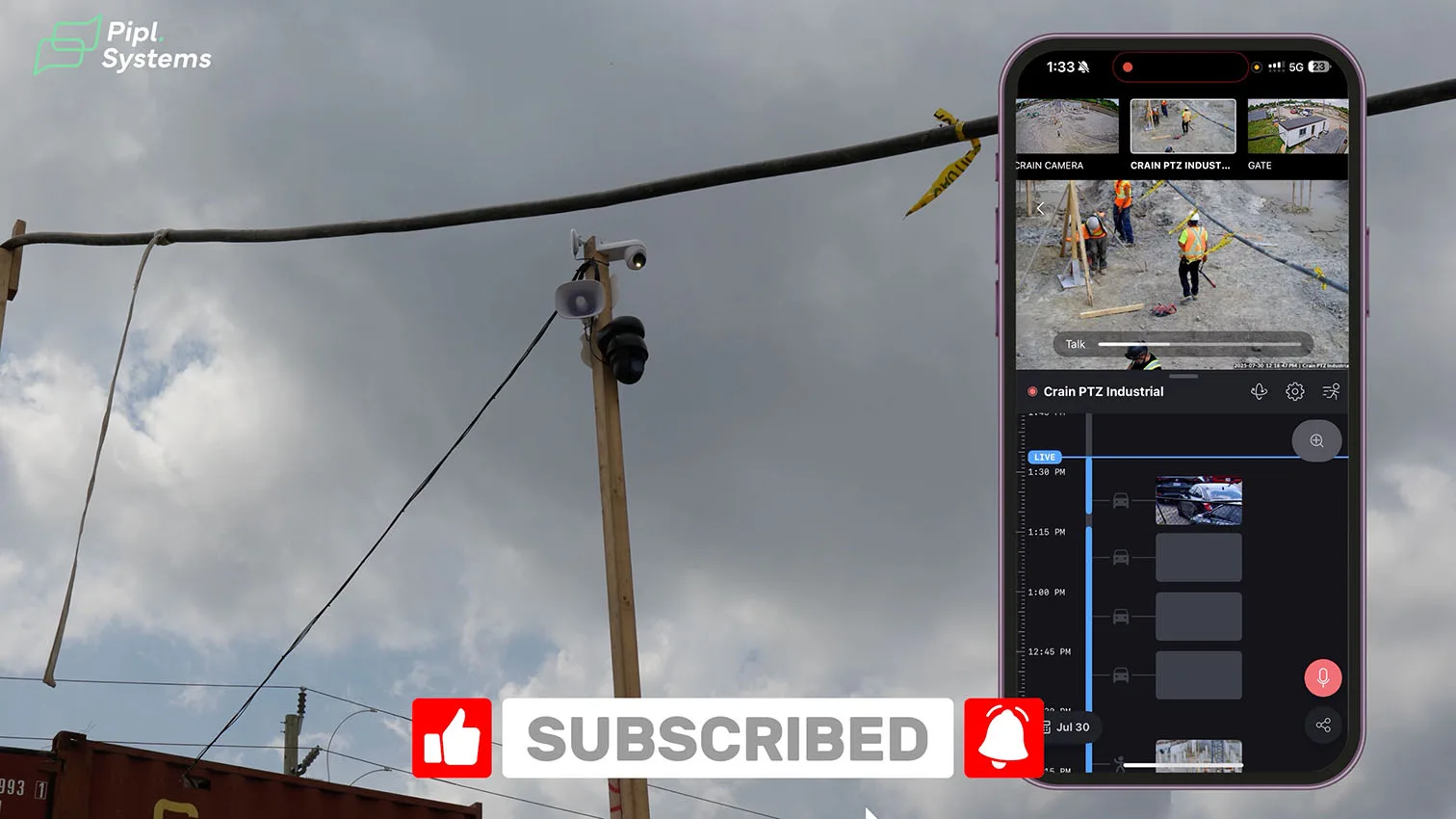
In UniFi Protect, Helder Luis (AIM Security) shows three panes that matter on a construction security case study like this:
- Devices: AI PTZ Industrial, AI Turret, and both AI Horn Speakers appear online with link quality, IPs, and live thumbnails.
- Live View: operators can steer the PTZ, check the crane line, and use two-way audio directly from the Protect UI.
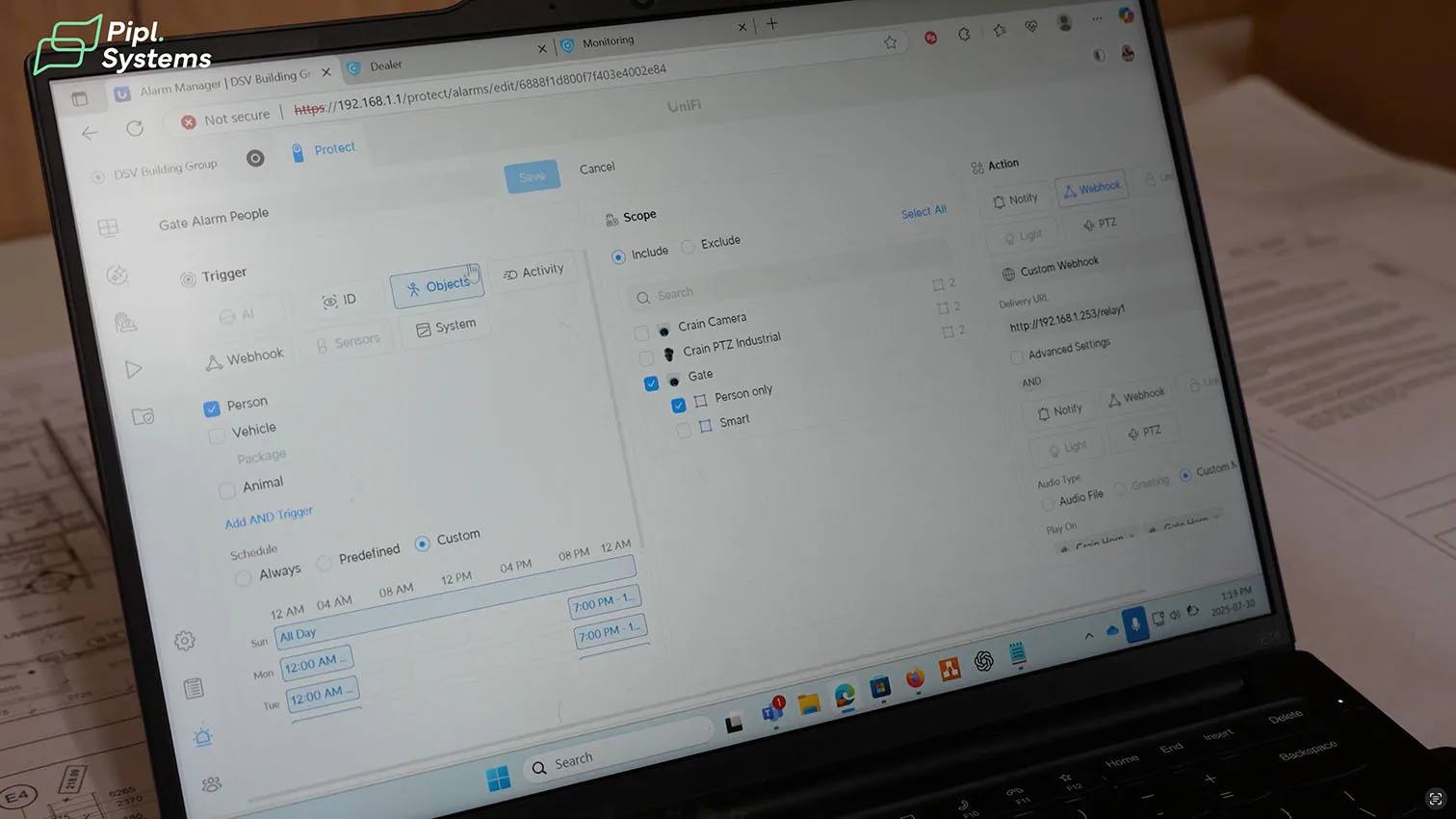
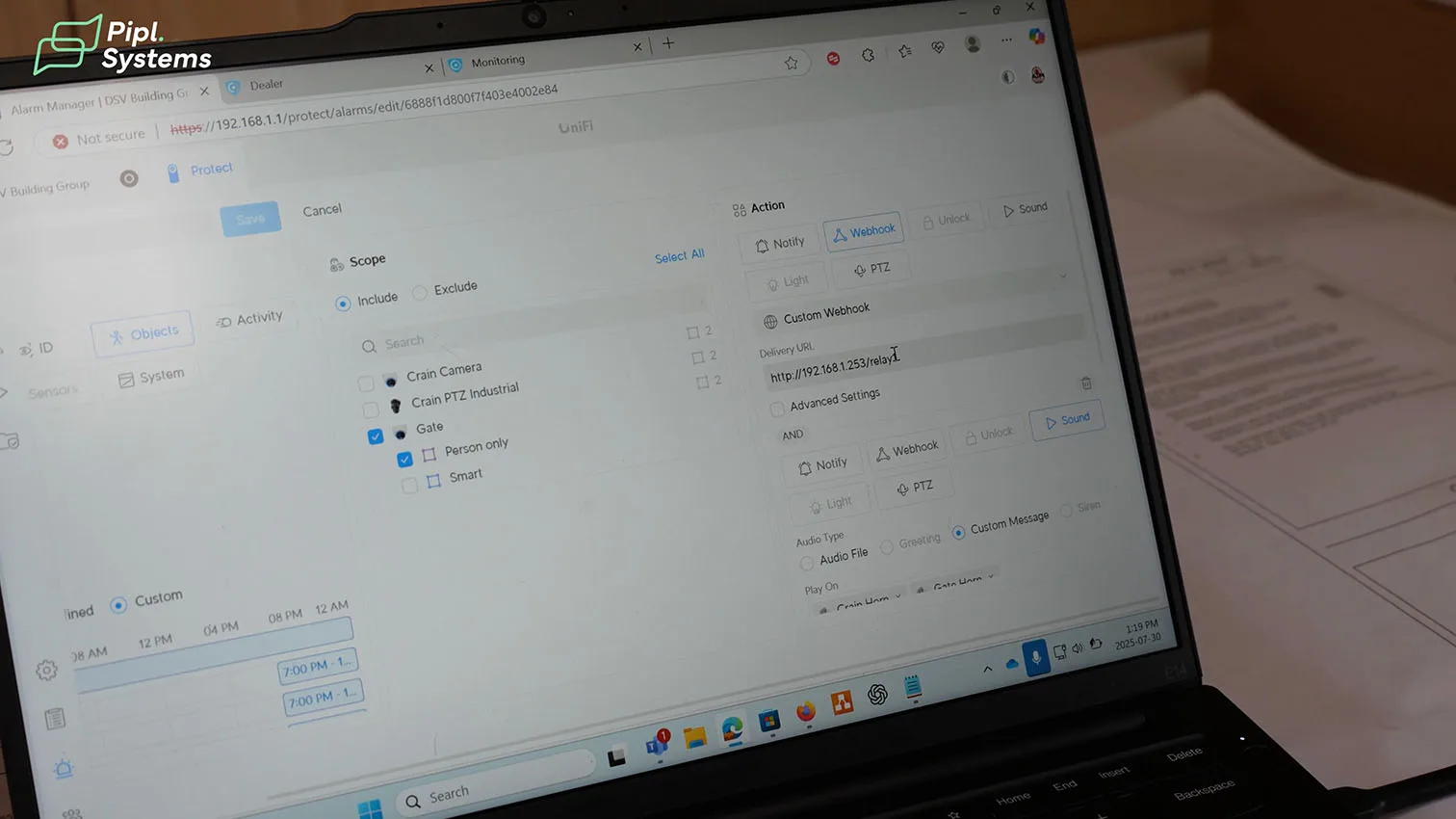
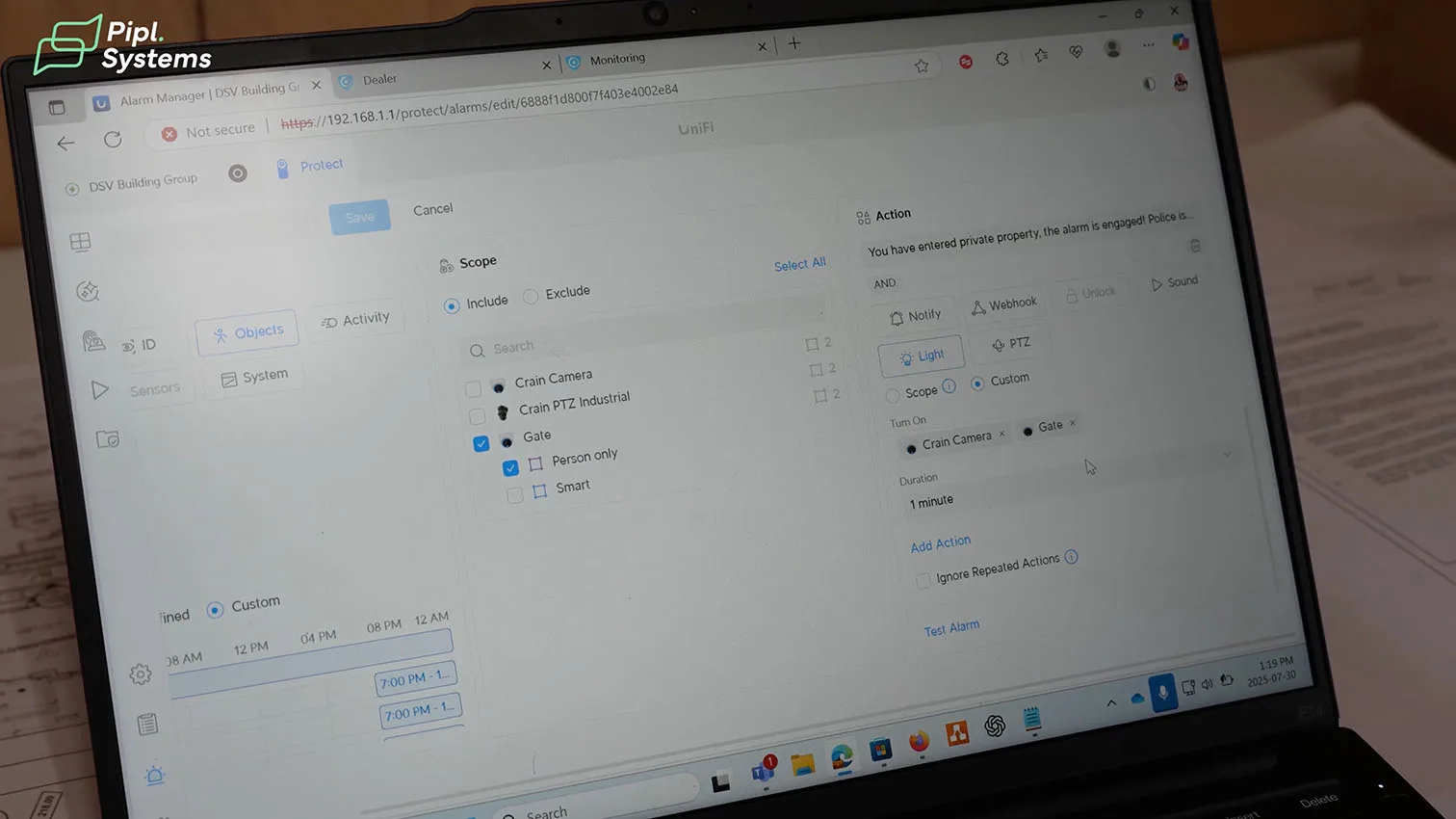
- Alarm Manager: a “Person only” rule watches a geofenced area after hours. The action stack includes a custom webhook (to the Opta relay), Sound (play deterrence message on both horns), Light (enable camera spotlights for 60 seconds), and optional PTZ action. This aligns Protect’s AI events with the downstream video alarm system.
Event Flow to the Alarm Monitoring Center
Detection chain, step-by-step:
- An AI security camera flags a person in the restricted zone.
- UniFi Protect triggers a custom webhook.
- The Arduino Opta closes a relay into the CHeKT bridge.
- The CHeKT bridge generates a video alarm event, pairs it with the live/recorded stream, and forwards it for CHeKT video verification.
- The alarm monitoring center receives instant visuals for decision-making and dispatch, while the site gets an immediate horn message.
This is the core of CHeKT visual security: alarms always ship with eyes-on video.
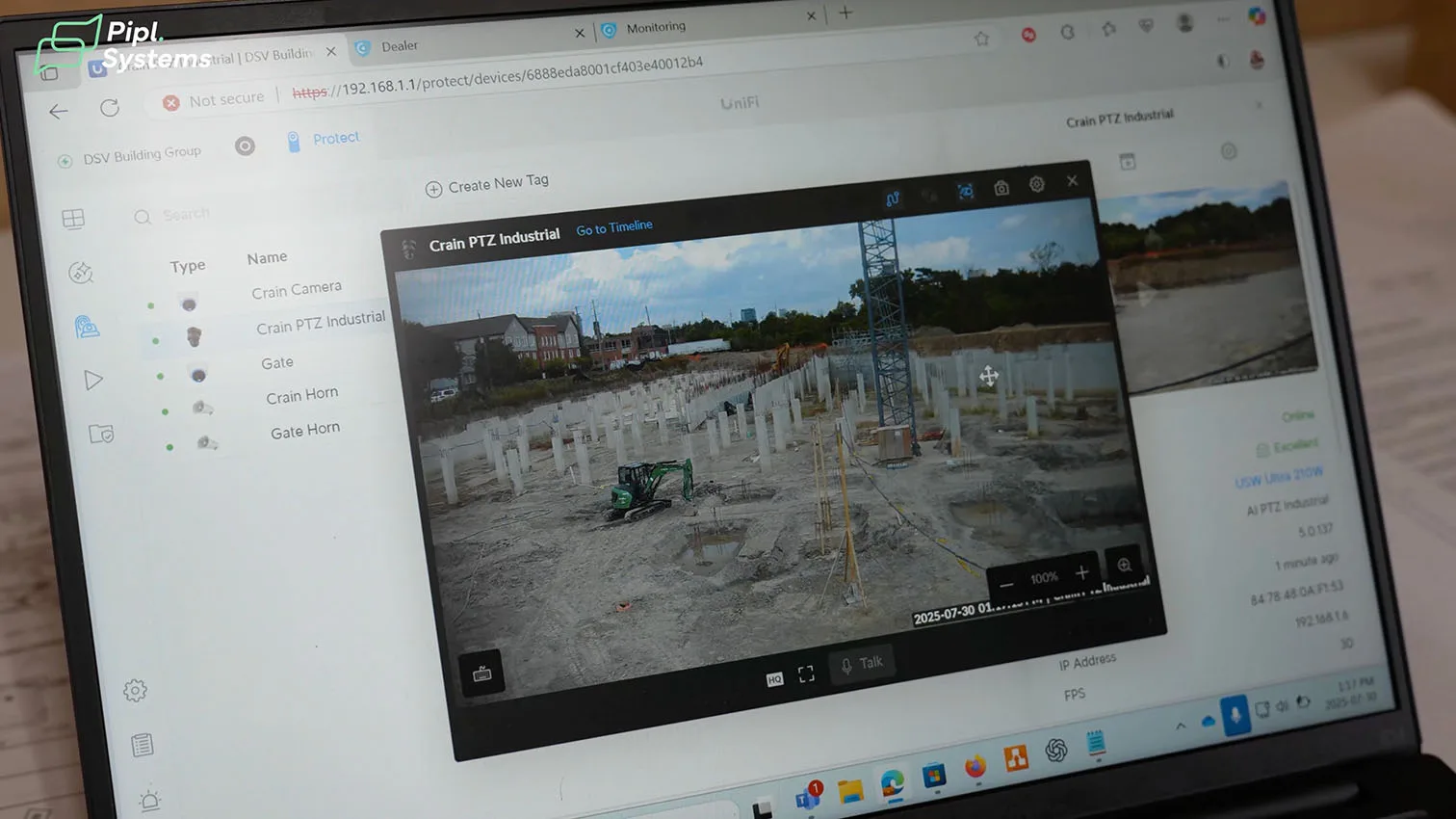
PTZ Patrol and Coverage Strategy
Automated patrol routes on the AI PTZ Industrial sweep the crane, staging lanes, and storage areas. Fixed AI cameras pin down chokepoints the PTZ might miss during a sweep. Together they minimize blind spots while keeping the rule set simple: person detection after hours, vehicle detection as needed at the gate.
Resilience, Storage, and Reality Checks
Local recording runs on the UDM-SE’s internal drive; if WAN drops, footage and on-site actions keep running. Cellular WAN provides primary or backup path so CHeKT video verification and live video monitoring remain reachable. For access controls later, dry contacts on the Opta/CHeKT side can be expanded to trigger lights or lock relays without re-architecting the UniFi Protect cameras.
Alarm Integration with CHeKT App
What the operator actually does
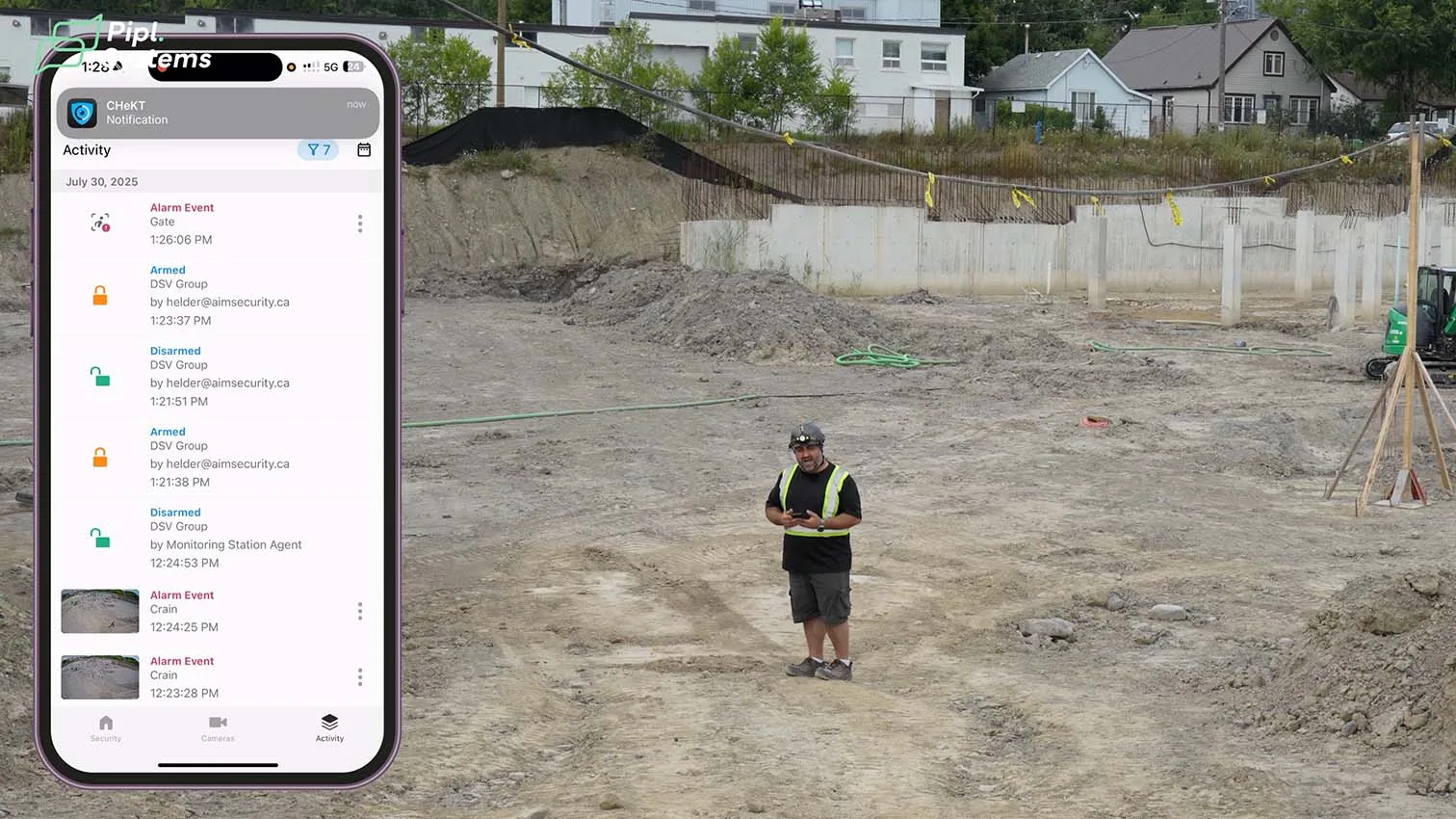
Arming and disarming happen in the CHeKT mobile app. Crews finish the shift, tap Arm, and get a confirmation push. As Helder Luis explains, “Everybody leaves the site, they arm it. You get a notification – it’s armed.” Supervisors can override the schedule for special work windows, keeping the system usable on dynamic North American job sites where hours change with deliveries and weather.
Detection zones and time windows in UniFi Protect
Inside UniFi Protect Alarm Manager, the team defined object-based rules for Person events only, then drew polygons over the restricted crane footprint and gate approach. Schedules restrict those rules to off-hours, which cuts nuisance events from daytime activity. Fixed AI turret cameras cover the approaches while the AI PTZ Industrial parks on a wide overview and auto-patrols for after-hours sweeps, supporting a video-centric security system without blind spots.
Custom webhooks that drive real alarms
Because UniFi Protect doesn’t natively talk to monitoring centers, AIM Security added a lightweight automation layer:
- UniFi Protect fires a Custom Webhook on qualified detections.
- An Arduino Opta (micro-PLC) receives the webhook and flips mapped relays.
- Those relays land on the CHeKT bridge zone inputs, turning analytics into a true video alarm system.
This design keeps UniFi analytics at the edge while CHeKT video verification handles event routing to the alarm monitoring center. Power is delivered via a PoE splitter, so the Opta and bridge keep running on the same protected UPS circuit as the switching gear.
What happens the second a person enters the zone
The moment a person crosses into the crane exclusion area, the workflow is automatic:
- UniFi Protect confirms a Person event in the defined polygon.
- The webhook trips the CHeKT bridge zone.
- CHeKT visual security pushes an alarm with live video to operators for video verification.
- UniFi automations run in parallel: camera LEDs turn on for 60 seconds and the AI Horn Speaker plays a custom warning (“You have entered private property. The alarm is engaged. Police are on the way.”).
- The AI PTZ Industrial snaps to a preset for close identification, then returns to patrol.
Latency is low enough for real-time decision-making, which matters when police dispatch requires verified visuals.
Real-world demo on site
During the filmed intrusion test, an actor stepped into the fenced crane zone. The system armed state in the CHeKT app flipped to active, a push arrived, lights came on, the horn broadcast the warning, and operators received the clip and live feed for video verification. That single event chained UniFi Protect analytics, the custom webhook relay, the CHeKT bridge, and the monitoring workflow—exactly what off-hours construction site security needs.
Practical setup tips for North American job sites
- Define separate zones for safety (crane swing, lifts, pits) versus theft risk (tool cribs, fuel). Use different audio messages and call trees.
- Keep horn output under local noise-bylaw limits; schedule quiet hours for nearby residences.
- Use dual connectivity (primary cellular + temporary broadband where available) so CHeKT alerts continue during ISP outages.
- Name devices by location (“Gate Horn,” “Crane PTZ”)—it speeds operator response.
- Review false alarms weekly; tighten polygons and confidence thresholds rather than disabling analytics.
- Coordinate with access controls at gates so arming aligns with crew check-out.
For readers who are new to the UniFi Protect ecosystem or want a complete walkthrough of choosing the right console, NVR, cameras, and PoE switches, we recommend checking out our in-depth UniFi Protect Guide for Beginners. In it, we break down every step of the process, from selecting the best hardware for your needs to configuring your system for maximum security and reliability. Alternatively, you can watch our detailed YouTube video on the same topic right below to see the setup in action:
Alarm Trigger Demonstration
h3 What was simulated and why it matters
To validate the video alarm system on an active North American construction site, Helder Luis (AIM Security) staged an after-hours intrusion at the perimeter office container. The objective was simple: prove that a person entering a restricted zone is detected in real time, warned on-site, and escalated to an alarm monitoring center for video verification without delay.
Step-by-step: from motion to dispatch
- Detection at the edge
• A UniFi Protect AI camera (fixed AI Turret) and an AI PTZ Industrial camera watch the gate and crane approach.
• Entering the geofenced zone triggers person detection. The camera’s onboard AI classifies a human target and timestamps the event. - Instant alarm automation
• The camera’s event calls a custom webhook.
• That webhook drives the CHeKT bridge relay, converting analytics into a supervised alarm signal for video-centric monitoring.
• In parallel, the system fires local deterrence: the AI Horn Speaker plays a pre-recorded “Private property—police en route” message and the camera’s light turns on for one minute to flood the scene. - Live video verification
• The same moment the horn sounds, live video monitoring appears in the CHeKT app. Operators see the exact camera, the clip leading up to the trigger, and the live feed for situational awareness.
• The bridge packages the event for the central station so an agent can perform video verification—confirming a real person in a no-go area versus wind, wildlife, or shadows. - Decision and response
• With verification complete, the monitoring team follows site response rules: talk-down via horn (if enabled), contact on-call staff, and request law-enforcement dispatch for a verified intrusion.
• All actions—trigger, talk-down, acknowledgment, and dispatch notes—are logged with time stamps.
What appeared in the app during the demo
• Large “Armed/Disarmed” control indicated system state.
• Push alerts arrived the instant the restricted zone was breached.
• Tapping the alert opened the event: short pre-/post-recording clip, live view, device list (AI cameras and horns), and a clear timeline of actions taken.
Results seen and heard on site
• The floodlight illuminated immediately, creating usable color video of the subject.
• The AI Horn Speaker broadcast the deterrence message loudly enough to be heard across the yard, signaling that the site is monitored.
• The PTZ resumed its patrol after the event, ensuring ongoing coverage of the crane and approach lanes.
Operator workflow that reduces false alarms
• Person-only analytics and tight polygons limit nuisance triggers.
• Webhooks tie only critical events to the CHeKT bridge, so the station receives fewer—but higher-value—alarms.
• Video verification ensures responding officers are dispatched on confirmed intrusions, aligning with best practices for construction site security and local false-alarm ordinances.
Takeaways for similar projects
• Pairing UniFi Protect analytics with a CHeKT bridge turns cameras into alarm points without losing high-resolution recording or PTZ control.
• Local deterrence (lights + horn) plus remote verification is the fastest path from detection to decision.
• For dynamic job sites, UBB wireless bridges and PoE at the edge keep devices connected without trenching, while maintaining the reliability needed for a video-centric security system.
If you are exploring advanced perimeter surveillance options or need a single camera that can reliably cover large outdoor areas, our detailed hands-on review of the UniFi Protect AI PTZ Industrial is a must-read. In this article, we put the camera through rigorous testing in a real farm environment to see if it truly lives up to its promise of replacing multiple fixed units with one AI-powered PTZ system. You can read the full review for technical insights, installation tips, and real-world performance results. Or, if you prefer, watch our in-depth YouTube video on the same topic right below to see the camera in action:
PTZ Patrol and Audio Warning
How continuous PTZ patrol secures a moving jobsite
The AI PTZ Industrial camera in this build runs an automated patrol using pre-set waypoints that sweep the crane base, access roads, and staging zones. Patrol dwell times and zoom levels are tuned to hold on likely entry paths, then widen out for situational awareness. This approach keeps coverage dynamic on a large, constantly changing site where fixed viewpoints can miss movement at the perimeter.
Voice-down deterrence that actually stops intrusions
When UniFi Protect flags a person inside a restricted zone, a custom webhook trips the relay on the CHeKT bridge and the AI Horn Speaker plays a pre-recorded warning. Helder Luis demonstrates the message used on site: “You have entered private property. The alarm is engaged. Police is on its way.” The immediate, authoritative announcement is paired with strobe/white-light activation on the AI camera for visibility.
Integrated lighting and alerting for night and low-contrast conditions
The PTZ’s patrol schedule extends into off-hours with automatic scene lighting from the camera’s integrated illuminators. This helps the analytics maintain person/vehicle classification accuracy and ensures the horn message is delivered into a lit scene that’s clearly captured for video verification.
End-to-end workflow during a live event
- AI object detection fires in UniFi Protect on the patrolling PTZ or a nearby fixed AI camera.
- A custom webhook calls the Arduino Opta, which closes a relay into the CHeKT bridge.
- CHeKT converts that input into a video alarm event, pushing live and recorded video to the alarm monitoring center for video verification.
- Simultaneously, the AI Horn Speaker broadcasts the voice warning and camera lights engage; push notifications appear in the CHeKT app for on-site managers.
- Operators verify the event and, if warranted, dispatch law enforcement with visual evidence.
Why patrol plus audio matters for construction site security
A moving crane, shifting stockpiles, and temporary fencing create blind spots if cameras sit static. Patrol closes those gaps, while voice-down immediately changes intruder behavior and reduces the need for guard rolls. Coupling this with CHeKT visual security and video verification gives the monitoring team what they need to authorize a response.
Wireless-first, built for temporary poles and changing layouts
Patrol routes include viewpoints connected over UBB wireless bridges, so the PTZ can cover distant poles without trenching. This is critical on active sites where hard conduit isn’t practical and layouts change week to week.
Configuration tips from field deployment
• Create distinct patrol profiles: daytime “observe” and off-hours “enforce,” each with different dwell/zoom.
• Script concise horn messages that state trespass status and consequence once, then repeat after a short interval to avoid noise complaints.
• Use privacy masks on neighboring properties and busy streets to limit nuisance triggers.
• Test voice audibility at perimeter lines and near equipment cabins; adjust horn angle and mounting height accordingly.
Outcomes seen in the demo
The PTZ reacquires the subject during patrol, the horn plays the custom message, lights engage, and the CHeKT app logs the alarm event with clips for review. At the same moment, the alarm monitoring center receives the video alarm system event for quick verification and potential dispatch—exactly the behavior required in a video-centric security system for high-risk construction zones.
If you are considering upgrading your home surveillance setup, our expert guide to the Top 5 Best NVR Security Systems for Home in 2025 will help you make an informed decision. We break down each system’s strengths, ideal use cases, and performance characteristics so you can match the right solution to your property’s security needs. From AI-driven detection to storage capacity and ease of installation, we cover the factors that matter most to homeowners. You can read the complete article for a detailed comparison and professional insights into the best options available this year.
Live Voice Broadcast via AI Horn Speaker
How real-time voice-down works from anywhere
The AI Horn Speaker enables live voice broadcast over the jobsite so supervisors or monitoring agents can speak directly to intruders or crews. Operators open UniFi Protect, select the horn device (or the paired Unifi Protect cameras at that pole), tap the microphone control, and hold to talk. Audio travels over the same secured network path as video, so voice and live video monitoring stay synchronized for fast intervention.
Operator workflow in the UniFi Protect interface
- Launch UniFi Protect and choose the relevant device group for the gate or crane zone.
- Confirm the scene on the AI PTZ Industrial or fixed AI camera tile.
- Tap the microphone icon to start a push-to-talk session to the AI Horn Speaker; release to listen.
- If the event is an off-hours trespass, trigger the pre-recorded warning, then follow with a custom message that references the site by name and the consequence of remaining on property.
- Document the interaction in the incident log; the CHeKT bridge will already have created the video alarm system ticket for the alarm monitoring center via video verification.
Field-tested use cases for immediate response
Safety instructions to crews during crane lifts when radios are busy.
Voice deterrence for perimeter breaches detected by AI cameras.
Wayfinding for deliveries after dark without sending a guard.
Live coordination with first responders while the CHeKT visual security clip and map location are on screen.
Best practices for reliable, clear broadcasts
Set horn angle to cover approach paths, not the trailer wall.
Limit custom messages to 6–10 seconds; repeat once after a short pause.
Use separate profiles for day and night volume to avoid noise complaints.
Keep an alternative path open (cell failover or UBB wireless bridges) so voice remains available during ISP outages.
For readers interested in exploring the latest advancements in AI-powered surveillance, we’ve prepared a comprehensive guide to the Best AI Security Cameras for 2025. This resource covers the most innovative models available, their intelligent detection capabilities, integration options, and performance in real-world conditions. Whether you are looking to secure a residential property or a commercial site, our article provides in-depth comparisons to help you choose the right AI camera for your needs. You can read the full guide or, if you prefer, watch our detailed YouTube video on the same topic, embedded below for your convenience:
Final Thoughts
What this deployment proves
AI-powered detection from UniFi Protect, paired with the CHeKT bridge, delivers a video-centric security system that does more than record. It creates verified video alarms, routes them to an alarm monitoring center, and adds live voice capability that changes on-site behavior in real time. The wireless-first backbone using UBB wireless bridges fits the fluid reality of North American construction sites where trenching isn’t feasible.
Why the integration matters
AIM Security’s custom UniFi-to-CHeKT integration—engineered by Helder Luis and team – bridges analytics and alarm transport without sacrificing local recording quality. Webhooks from Protect drive the Arduino Opta relays, which feed the CHeKT bridge; the result is fast, auditable CHeKT video verification with access to live views, clips, and two-way audio. It’s a practical, market-ready construction security solution that aligns with how general contractors operate across the U.S. and Canada.
Key takeaways for jobsite stakeholders
Design around high-risk zones first (crane base, material staging, access roads).
Use AI PTZ Industrial patrols to close blind spots and confirm intrusions before dispatch.
Standardize pre-recorded voice warnings, then layer in live talk-down when needed.
Keep storage and bandwidth local when possible; escalate only verified events upstream.
Choose components that survive mud, vibration, and weekly layout changes.
This case study demonstrates how CHeKT visual security, Unifi Protect cameras, an AI Horn Speaker, and an AI PTZ Industrial camera combine into a cohesive construction security solution—providing fast alerts, clear audio warnings, and reliable evidence for law enforcement when an incident truly requires it.
FAQ Section
Common Questions About Construction Site Security with UniFi Protect and CHeKT
How does live voice broadcast improve construction site security?
Live voice broadcast through an AI Horn Speaker allows security personnel or monitoring agents to speak directly to individuals on site in real time. This can be used to deter trespassers, give instructions to authorized workers, or coordinate emergency responses without physically being present.
Can UniFi Protect cameras integrate directly with alarm monitoring systems?
By default, UniFi Protect does not natively transmit video to central alarm stations. However, with a CHeKT visual security bridge and a custom integration, video from UniFi cameras can be linked to alarm events, providing verified video to monitoring operators for faster, more informed responses.
What are the benefits of using AI-powered detection in high-risk zones?
AI detection reduces false alarms by distinguishing between people, vehicles, and environmental movement. In high-risk zones such as crane areas, this ensures that only relevant intrusions trigger alerts, improving efficiency and reducing unnecessary dispatches.

Is wireless deployment reliable for large or temporary job sites?
With point-to-point wireless bridges like UniFi UBB, it is possible to deliver stable, high-bandwidth connections across large construction sites without trenching. This makes it ideal for temporary or changing layouts, as the system can be redeployed as the site evolves.
What types of storage are recommended for these deployments?
Most sites use local storage on the UniFi NVR or Protect appliance for primary recording, with optional cloud or offsite backups for redundancy. For critical security zones, it’s important to ensure storage is sized to retain at least 30 days of footage.
How does this solution meet North American security standards?
This integration meets common North American security industry practices by incorporating UL-listed alarm monitoring equipment, tamper-proof installation, and real-time verification workflows that align with central station operating procedures.